How our award-winning MDR service helps protect businesses from hackers by becoming an extension of in-house resources
There is no silver bullet to prevent 100% of cyber-attacks. With firewalls, antivirus and intrusion prevention systems only capable of stopping the most common cyber threats, it is vital that businesses have the ability to detect breaches and remediate them before they cause serious financial and reputational damage.
However, in-house log monitoring to detect suspicious activity is complex and time-consuming, requiring skilled security experts who are in high demand and expensive to recruit. The huge cost of setting up an in-house cyber security operations centre (CSOC) means that this is rarely a viable option for many organisations.
The benefits of an outsourced CSOC service
ThreatDetect™ is an outsourced, fully-managed detection and response service (MDR) designed to offer businesses of all sizes the capability to detect and remediate threats without a need for huge capital expenditure
By integrating cutting-edge detection technology, up-to-the-minute threat intelligence and expert human analysis into a monthly Opex service, ThreatDetect acts as a virtual extension of in-house IT resources to supply the tools and expertise needed to hunt down and remediate malware and viruses as well as the latest brute force and social engineering attacks.
With ThreatDetect, businesses can reduce cyber security risk through increased threat visibility, enhanced breach detection and rapid incident response.
Learn more about our ThreatDetect MDR service.
Supplementing existing security capabilities
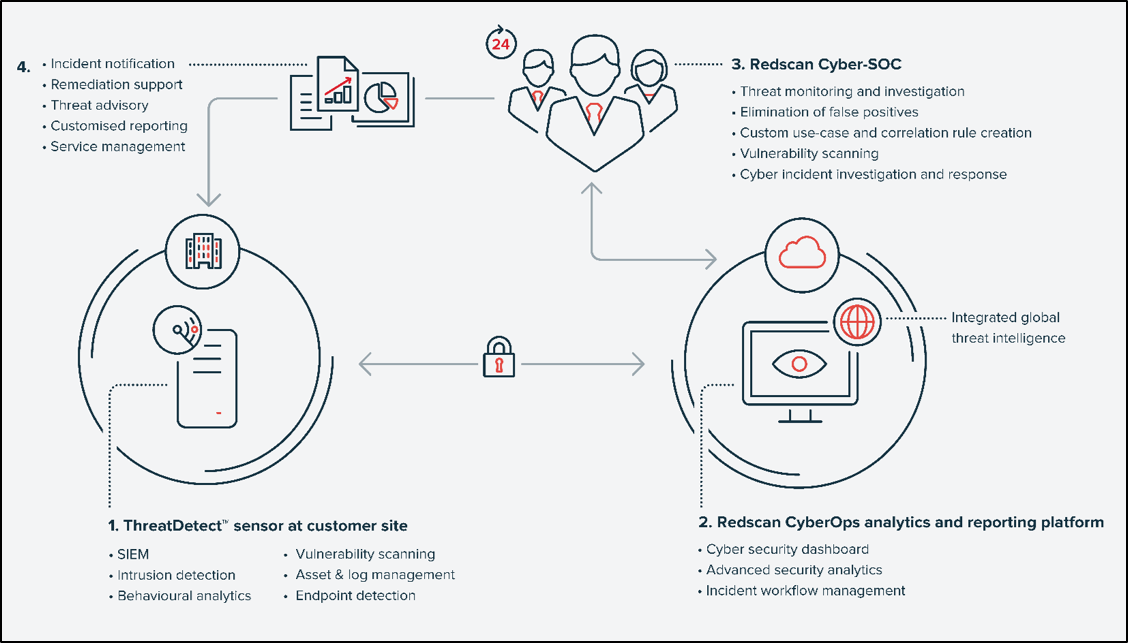
The illustration below explains how ThreatDetect is deployed within a business to provide the swift incident notification and remediation advice in-house IT and security teams need to respond to and neutralise threats.
- The core monitoring platform underlying ThreatDetect is comprised of loggers and sensors that collect information about activity across an organisation’s network. Platform functionality includes security information and event management (SIEM), intrusion detection, asset management and endpoint detection. This platform supports physical and virtual deployments and can be installed on-premise or accessed via Redscan’s fully resilient cloud.
- The CyberOps threat notification and analytics platform included as part of ThreatDetect receives incoming alarms from the underlying monitoring systems. These alarms are generated using behavioural analytics and advanced correlation rule sets that are designed to identify suspicious network events and patterns of behaviour. Alarms are raised for the attention of the Redscan CSOC.
- A 24/7 CSOC is the heartbeat of ThreatDetect. Redscan’s in-house team of security analysts, engineers and researchers use proven threat investigation methodologies and aggregated threat intelligence from internal and external sources to monitor and investigate pending security alarms. Once assessed, genuine alarms are raised to end customers via CyberOps’s intuitive incident workflow and delivered with clear remediation guidance.
- By thoroughly investigating threats and offering helpful remediation assistance, the Redscan CyberSOC cuts through over-flowing security alarms to pinpoint threats, prioritise incidents and provide the level of support needed to achieve swift and effective incident response. By receiving recommended remedial actions, customer IT teams are able to focus on fixing rather than discovering threats.
ThreatDetect customers also benefit from full access to CyberOps analytics and reporting tools. By providing a wide range of security and activity widgets, CyberOps enables organisation to obtain a live overview of security status. This information is supplemented with regular custom security status reports produced by the Redscan CSOC.


