Overview
The threat landscape has changed significantly in recent years with Malware becoming increasingly sophisticated and adept at evading Antivirus software. A recent example is UPS who were infected by malware that anti-virus software did not detect. The Redscan Security Research Team tested a number of techniques for injecting malicious code to determine how reliably we could evade commercial Antivirus solutions. The reasons for doing this are twofold:
- We perform penetration testing for customers and depending on the engagement, sometimes need to covertly install software to emulate the tasks an attacker would perform;
- We regularly test the effectiveness of security controls to ensure that our customers have the most effective protection mechanisms in place.
The code tested does not exploit vulnerabilities in software, but merely allows attackers to stay resident on a victims system after it has been compromised. It should be mentioned that the code produced is deliberately not very sophisticated and uses a number of well-trodden techniques to make life easier for the anti-virus programs. The results are a concern as they illustrate how easy it is using easily accessible tools and remarkably little time, to usher malware past anti-malware software.
Methodology
Using existing knowledge and available packages, we produced some malware and then obfuscated the code using a number of different techniques. To test detection rates by anti-virus solutions, the malware we produced was scanned against 53 anti-virus programs from all major vendors to ensure comprehensive results.
Metasploit Reverse TCP Shell
To begin with we generated malicious code using the popular Metasploit framework. The code produced connects back to an attackers machine in an attempt to evade firewalls without egress filtering. Once connected the attacker has full shell access to the victim’s machine. Antivirus Detection rate: 33/53 vendors detected this executable as malware.
Metasploit Reverse TCP Shell (encoded)
In an effort to reduce our detection rates we ran the Metasploit backdoor though multiple msfencode routines. This actually resulted in antivirus software being more likely to detect the executable as being malicious as they detected the obfuscation techniques used by msfencode. Detection rate: 36/53 vendors detected this executable as malware.
XOR Encryption Routine
Antivirus software typically scans files on disk rather than executables in memory, since this is less computationally intensive. To exploit this trait, we took a known malicious binary and injected some additional code into an unused portion of the text segment (and made this segment executable). The code below encrypts the data segment of the binary using an XOR algorithm with a fixed key. Once the binary has been encrypted we save it to disk within our debugging environment. 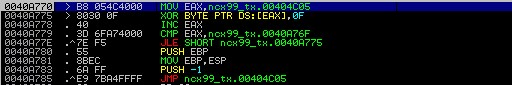
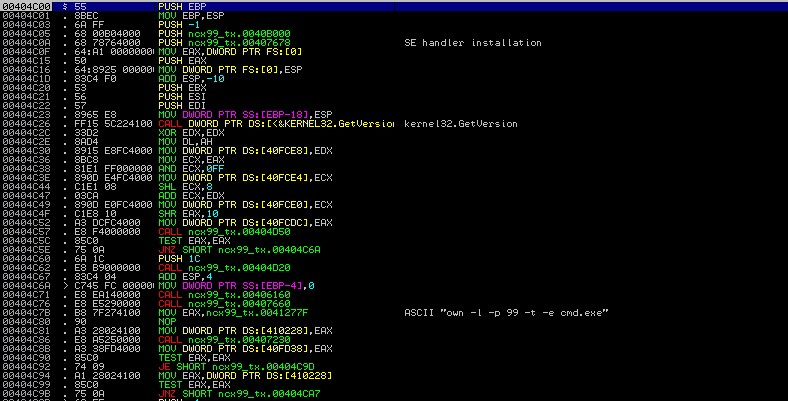
Backdoor Existing Executable
For this test, we added a new segment to a legitimate executable and rerouted the execution flow using a JMP statement. We used a free TFTP server as this already contained networking code, it wouldn’t seem unusual that it would creating additional network sockets. Detection rate: 15/53 vendors detected this executable as malware.
UPX Packing
UPX is a popular binary compression system used to reduce the size of executables. Since it alters the binary signature of the executables, it can allow us to evade signature based detection. Detection rate: 31/53 vendors detected this executable as malware.
Compiled Python Executable
We created a python script to connect to a webserver and execute commands it was provided. The script was compiled using PyInstaller into a Windows executable. This resulting executable was not detected by any antivirus product, however since the executable was almost 11MB this wouldn’t be particularly scalable for targeting large numbers of users. Detection rate: 0/53 vendors detected this executable as malware.
Epsilon
Epsilon is a custom Trojan created by Redscan, designed for use during our penetration testing engagements. It has a large number of features including keystroke logging, firewall evasion, file transfer and desktop screenshots. The resulting executable is around 400Kb. Detection rate: 2/53 vendors detected this executable as malware.
Conclusion
Antivirus detection rates against malware of this type are not particularly promising. It could be easily imagined that by tweaking the algorithms used here, targeted attacks could be quickly successful. Using multiple antivirus engines results in much higher detection rates, which shows the importance of using detection engines from multiple vendors. Do not believe the hype that these systems are obsolete, they form a significant part of any defensive posture. However, the problem illustrated here is that anti-virus software cannot be 100% effective. It is too easy to write a solution that will slip past a vendor so a strategy of proactive monitoring needs to be adopted. But, all malware will leave a footprint within an organisation, the aim is to detect this footprint so today’s more sophisticated malware can be identified. This can be done by monitoring the traffic and the events generated by systems on the network, analysing behaviour over time and alerting when suspicious behaviour is recognised.


