While phishing-as-a-service is not a new concept, Microsoft’s recent analysis of the BulletProofLink campaign highlights that threat actors are now treating it as a fully-fledged business.
In this blog post, we outline how the campaign works and the steps organisations can take to reduce the potential risks created by this and other email-based attacks.
What is phishing-as-a-service?
Phishing is one of the most common attack vectors used by cybercriminals. By creating emails that imitate those of trusted individuals and organisations, they aim to encourage users to click malicious attachments or links or divulging sensitive information.
Malicious phishing-as-a-service is the next stage in the evolution of this type of cybercrime, in which the capability and the resources required to execute these threats are packaged and sold as a commodity to anyone willing to pay.
What is BulletProofLink?
Microsoft recently published an investigation into the BulletProofLink phishing campaign that reportedly utilised over 300,000 sub-domains in a single campaign. Researchers uncovered an extensive phishing-as-a-service marketplace which enables one-off or subscription-based methods for leasing infrastructure, phishing kits and methods for collecting and redistributing stolen credentials still in operation.
First discovered in October 2020 by OSINT Fans, BulletProofLink, also known as BulletProftLink or Anthrax, markets itself openly online. This even extends to posting ‘How-to’ videos on YouTube to show ‘customers’ how to take advantage of its tools. The Microsoft report reveals that the Bulletproftlink ICQ group chat had 1,618 members in 2020.
How do BulletProofLink campaigns work?
Phishing kits distributed via these campaigns are specifically crafted to bypass email threat detection technologies and are available for purchase as stand-alone products. According to Microsoft, one method that the actors deploy is zero-point fonts in the HTML of an email lure to pad the body text of the message and bypass scanning technology for in-line email defences.
The phishing templates are designed to steal credentials by masquerading as different products or technologies, as shown in the image below, a screenshot of the marketplace captured by Microsoft.
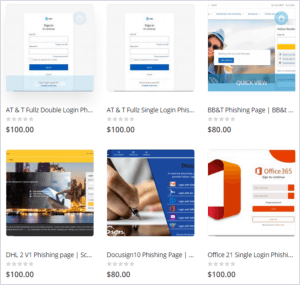
The hosting service provided by BulletProofLink includes domain reputation management, offering replacement domains if the current campaign is reported to be malicious by reputation services. Threat actors who purchase services from BulletProofLink receive the stolen credentials via a weekly shipment of log files containing the captured credentials, likely along with the connection IP, user agent and other identifying information about the user.
Infinite subdomain abuse
The infrastructure used to host the phishing sites that capture victims’ credentials utilises compromised websites and a technique known as ‘infinite subdomain use’. This allows the BulletProofLink actors to generate any number of subdomains for a single compromised domain, either by exploiting the DNS settings of a domain or leveraging misconfigured sites that have wildcarded subdomains.
Enabling double theft
It is notable that the type of large-scale phishing campaigns enabled by BulletProofLink use a “double theft” approach. This tactic, which is intended to increase the threat actor’s profits, involves the distribution of credentials stolen in phishing attacks to a secondary server controlled by phishing-as-a-service operators, provided the phish kits used in the campaign use their default configuration. If the cybercriminals do not customise the phish kits to exfiltrate stolen data to their own servers alone, the credentials they harvest are also sent to the operator. These credentials can help to fuel the growing market for initial access brokers.
The rise in email-based attacks
Email-based attacks remain one of the simplest and most cost-efficient ways for threat actors to target any organisation. Whether it is phishing for credentials or delivering malware as an attachment or link, it can be performed on a massive scale. Phishing-as-a-service providers significantly lower the barrier of entry to threat actors, who, with limited or no technical skills, can now start using phishing for a nominal fee.
While phishing-as-a-service is certainly not a new concept, Microsoft’s analysis of the campaigns shows that cybercrime actors now manage it as a fully-fledged business, with marketing, customer service and even discounts for subscribing to newsletters. With increased custom and revenue, templates and detection bypasses can become even more sophisticated.
While ease and scale make email-borne threats prevalent in the threat landscape, phishing campaigns are also effective, representing a good return on investment from an attacker’s point of view. Email compromise has made up 25% of Kroll Incident Response engagement cases so far this year. This highlights the fact that while phishing attacks, such as those sold by BulletProofLink, may appear on the surface to be simple, they are highly impactful and continue to be disruptive to business operations.
Mitigations
- Enable the Safe Links feature in Office 365 to perform real-time scanning and rewriting of URLs in inbound emails clicked by users.
- Consider implementing anti-phishing policies to protect users from spoofing, first contact emails and more.
- Ensure that users are aware of the threat posed by phishing and consider running phishing tests, either internally or through a third-party provider, to analyse click through rates and identify areas of concern.
- Employ Endpoint Detection and Response (EDR) and Next Generation Anti-Virus (NGAV) on all hosts for help with detecting where any phishing activity has been successful within the environment.
- Take preventative steps to practise for these scenarios such as blocking macros where they aren’t required.
How Redscan can help
Redscan’s social engineering services allow organisations to accurately assess the ability of their systems and personnel to detect and respond to phishing-as-a-service, spear phishing-as-a-service and Business Email Compromise. Our customised ethical hacking assessments provide specific insight into the potential risks while our phishing simulations accurately evaluate employee awareness of phishing email scams.




