Traditional antivirus solutions function by scanning files on disk. While this facilitates the detection of many common threats, more advanced forms of malware are at risk of being missed.
In this latest Redscan Labs article, we examine the process required to detect, analyse and respond to an increasingly prevalent cyber security threat that is capable of evading signature-based defences – memory-resident malware.
What is memory-resident malware?
Memory-resident malware, also known as fileless malware, is a type of malicious software that writes itself directly onto a computer’s system memory. This behaviour leaves very few signs of infection, making it difficult for traditional tools and non-experts to identify.
The problem of persistence
A common question pertaining to memory-resident malware is how, if only executed in memory, the malware continues to run when a user reboots the infected system.
Where a system restart is performed, most memory-resident malware has the ability to re-execute itself in memory using a number of mechanisms such as registry entries, WMI triggered events and background intelligent transfer service (BITS) tasks.
In instances where multiple domain controller systems are infected, re-execution might not be necessary at all, given that the chance of all systems being restarted at the same time is unlikely.
Memory-resident malware in action
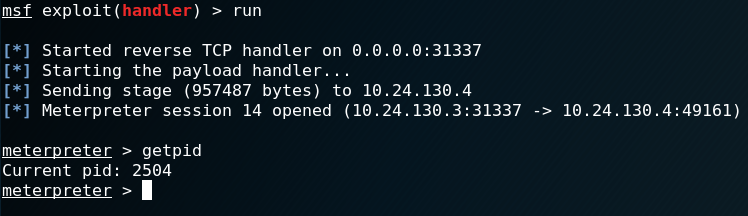
In the example below, a Meterpreter Trojan is purporting to be a PDF file.

When the infected file is opened, a legitimate PDF is dropped to local storage. The resident malware is subsequently uploaded to memory and deleted from the disk. As a consequence of this, the attacker responsible for the malware is now able to gain remote control of the compromised machine.
Malware detection and memory forensics
To detect memory-resident malware, it is essential that traditional antivirus is supplemented by technologies that facilitate volatile system memory (RAM) capture and continuous behavioural monitoring.
Organisations should look to Network (NIDS) and Host-based (HIDS) Intrusion Detection Systems, as well as Endpoint Analytics, to help identify indicators of compromise (IOCs).
Once memory-resident malware has been detected, further analysis is required to enhance response efforts and help configure security systems to pinpoint similar attacks in the future.
Forensic analysis of memory-resident malware can be achieved with a tool such as AccessData FTK Imager, which can capture a copy of an infected device’s memory contents for analysis.
Once a dump of the memory has been taken, it can then be transferred to a separate workstation for analysis. This ensures that the original system, which may be needed as evidence, is fully preserved. The workstation should not be connected to a network.
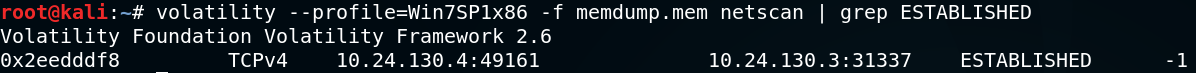
With a copy of the system’s memory, the Volatility Foundation’s memory forensics framework can then be used to help analyse its contents. An initial starting point could be to examine active network connections from the host:
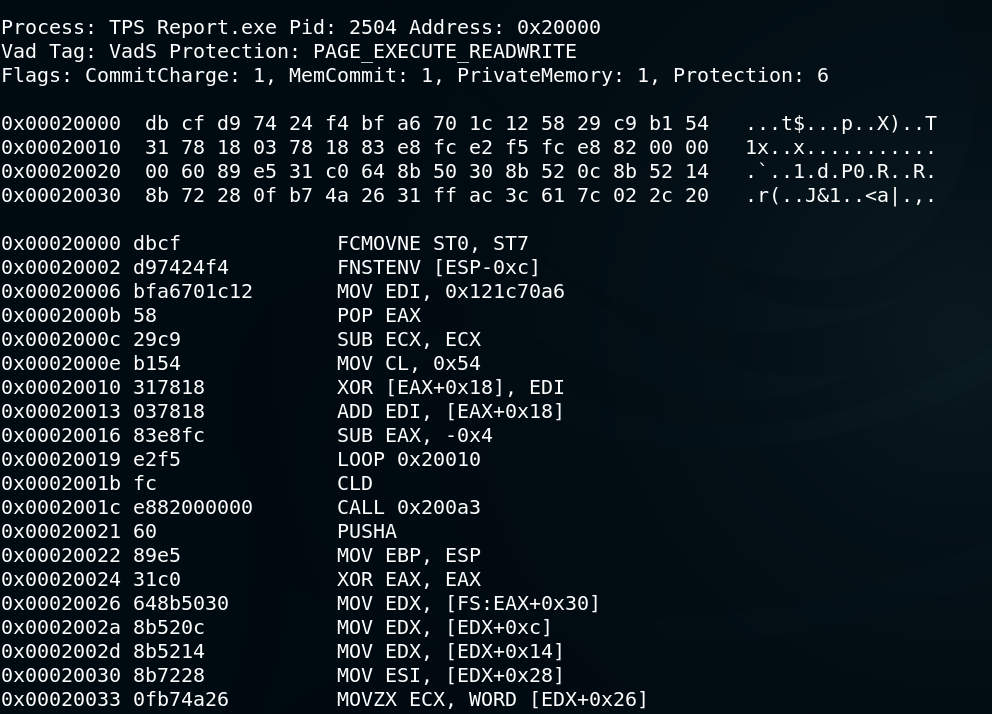
A subsequent action could be to run a plugin such as malfind to identify suspicious executables based on characteristics such as virtual address tree tags and page permissions.
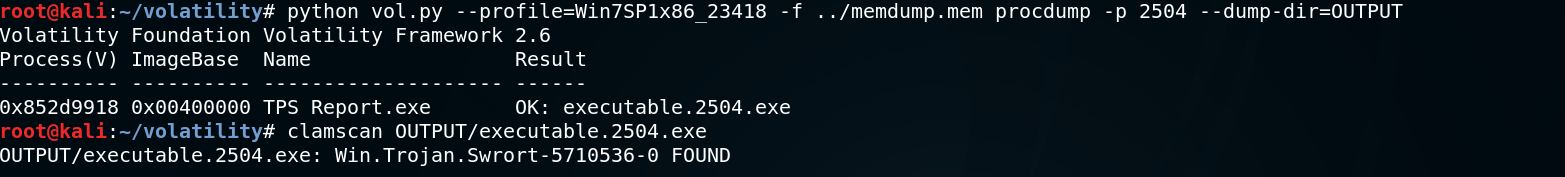
Once a suspicious process has been detected, the executable can then be extracted from the system’s memory, assessed with an antivirus scanner and, if neccesary, reverse engineered.
Note: memory forensics is a highly specialised process that if not conducted correctly has the ability to disrupt rather than aid an organisation’s response to cyber-attacks. Rather than risk losing vital evidence and facilitating the spread of an infection, organisations are advised to consult a threat detection and incident response specialist.
About Redscan Labs
Redscan Labs is a specialist hub within our cyber security operations centre dedicated to in-house threat research and analysis. By conducting regular threat investigation, such as in-depth malware analysis, our experts maintain an in-depth understanding of the latest malicious actors and use this knowledge to improve our range of award-winning security services, including proactive network and endpoint monitoring.
Useful resources:
Identifying and responding to threats
Redscan Labs: Malware unpacking – How to uncover hidden threats



