In the cyber security industry, there is a tendency for threat detection efforts to be measured solely for efficiency rather than genuine effectiveness.
Statistics routinely collected and assessed as part of network and endpoint monitoring include events per second, alerts and false positives, with success often benchmarked by the time to detect, respond and recover.
Incorporating scenario-based testing into the threat detection process allows organisations to obtain additional insight into the true effectiveness of detection and response controls and procedures by benchmarking performance against the attributes of specific types of attacks.
Scenario-based testing programmes are typically benchmarked against specific adversarial frameworks such as MITRE ATT&CK.
The MITRE ATT&CK Framework
Adversarial Tactics, Techniques and Common Knowledge (ATT&CK) is a knowledge-base developed by MITRE that describes the tactics and techniques used by adversaries to compromise networks and achieve their objectives.
The MITRE ATT&CK for Enterprise framework provides a foundation for organisations to use to develop threat models and methodologies to defend against common attacker behaviours.
MITRE ATT&CK is open and community-supported, allowing any organisation to utilise and contribute to it. ATT&CK intelligence is gathered through a combination of MITRE research and third party insight from offensive security engagements such as penetration testing and red teaming.
“A curated knowledge base and model for cyber adversary behaviour, reflecting the various phases of an adversary’s lifecycle and the platforms they are known to target” – MITRE
MITRE ATT&CK Tactics, Techniques and Sub-Techniques
The MITRE ATT&CK framework is divided into two main groups – tactics and techniques. Broadly speaking, these refer to the ‘what’ and ‘how’ of adversary tradecraft. Tactics are the overall objectives that an attacker is trying to achieve, while techniques are the specific actions they perform in order to achieve those objectives.
MITRE ATT&CK is periodically updated in order to reflect the changing threat landscape and better support organisations in developing their detection and response actions.
An update in July 2020 improved the framework by adding sub-techniques. Sub-techniques describe, in more detail, the ways in which techniques are implemented. For example, for the Credential Dumping technique, there are now nine sub-techniques that could be used.
Historically, the framework has focused primarily on the behaviours that adversaries perform once they’ve gained access to an environment, as this best aligned with the visibility that defenders would have of their own networks. However, this left pre-compromise behaviours uncovered, and a separate framework known as PRE-ATT&CK was developed to define the behaviours leading up to a compromise.
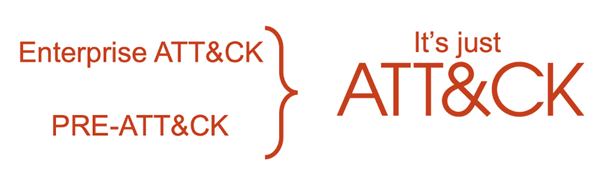
Another update (MITRE ATT&CK v8) in October 2020 consolidated the framework by incorporating PRE-ATT&CK into the broader Enterprise ATT&CK domain. Only behaviours which could be deemed technical in nature, visible to defenders and actively used in the wild were assimilated into ATT&CK. This resulted in two additional tactics being added – Reconnaissance and Resource Development.
The MITRE ATT&CK matrix for Enterprise now includes 14 tactics, with 205 techniques and 468 sub-techniques.
View the full Enterprise Matrix to see a breakdown of all the MITRE ATT&CK tactics, techniques and sub-techniques
Scenario-based testing in threat detection
Given that adversaries will likely utilise a wide range of methods throughout the course of an attack, no one tactic or technique is more important than the next, and defenders must be prepared to detect and respond to any and all malicious behaviour, in whatever sequence it occurs.
An effective way to utilise the MITRE ATT&CK framework to devise a threat scenario which utilises a specific set of techniques, with a single pre-defined objective. Typical objectives could include gaining access to domain admin credentials, accessing data from internal applications or simulating a ransomware infection.
Scenario-based testing will attempt to mimic the approach of real-word attackers by targeting business critical information and systems, using the attack vectors which are most relevant to the business in question.
By conducting this form of engagement, Red Team ethical hackers can evaluate the effectiveness of detection and response capabilities, highlight gaps in coverage and identify risks which require mitigation.
Example attack scenarios that could be assessed:
- Gaining access to a network and harvesting credentials via a phishing campaign
- Abuse of legitimate tools provided by operating systems to establish a persistent foothold, pivot throughout the environment, and obtain sensitive information
- Exploitation of software vulnerabilities and misconfigurations to increase privileges
- Exfiltration of sensitive information from the network via protocols that are widely used in the environment
Methodology of a scenario-based assessment
A scenario-based exercise aligned to the MITRE ATT&CK framework will typically follow the process below. Throughout this process, the Blue Team will be continually attempting to detect and respond to the techniques being utilised.
- Identify the pre-defined objective for the engagement
- Launch an attack using an established attack vector to gain a foothold in the target environment
- Conduct internal reconnaissance to establish situational awareness on where the objectives are, what defences are in place and which actions are likely to be detected
- Activities including persistence, pivoting and/or privilege escalation, depending on the path required to reach the objective
- Reach the objective
- Evaluate Blue Team performance and provide guidance on implementation
Stage six is an essential phase of the assessment process. Continuous review and improvement of threat detection techniques and processes is essential to ensure that security tools, processes and skillsets are continually optimised to defend against genuine attacks by swiftly identifying and eliminating breaches in their infancy.
The challenges of scenario-based testing
Regardless of size or industry, all organisations need a combination of red and blue team expertise to effectively combat cyber threats. The reality for many businesses, however, is that they lack the people and resources necessary to implement a scenario-based testing approach.
Many small and mid-market businesses don’t have a dedicated security team at all, and the responsibility often falls on already stretched IT personnel. Others have invested heavily into their in-house security operations, but don’t have the red team knowledge necessary to properly evaluate their effectiveness.
An outsourced security service can help to ease these worries by providing organisations with the specialist expertise and technology required to address their security needs.
Buyers should look for a service provider with experience in offensive security, capable of fostering a collaborative ‘purple team’ approach between red and blue team resources and integrating scenario-based testing into threat detection processes.
A specialist Managed Detection and Response (MDR) service that offers scenario-based testing can deliver significant benefits over a traditional managed security service, helping to maximise threat detection and incident response capabilities.
Watch our webinar for more information on how Scenario-Based Testing can help to evaluate your security defences
Why choose Redscan?
Redscan is an award-winning provider of cyber security services including MDR, Red Team Operations and CREST-accredited Pen Testing.
By utilising our deep knowledge of offensive security, alongside the latest security tools, technologies and scenario-based testing frameworks, we help organisations to identify, hunt for and eliminate threats and vulnerabilities across their networks and endpoints. Redscan Labs, our threat research and analytics division, utilises the ATT&CK framework to help provide actionable insight to improve the quality and effectiveness of our services.
Whether you are looking to incorporate scenario-based testing into your existing security operations, or invest in a fully outsourced service, you can be confident that Redscan will provide the high-quality insight and advice you need to significantly improve your organisation’s cyber security posture.
More on scenario-based testing




