Kroll’s latest threat landscape report highlights the impact of the CLOP ransomware gang’s exploitation of the MOVEit transfer vulnerability, and the rise in email compromise attacks.
These, as well as other key trends from the previous quarter, are discussed in the report, available to download here.
A complex threat environment
While CLOP ransomware activity dominated the headlines in Q2 2023, analysis of Kroll engagement data painted a more complex picture of the threat environment. CLOP activity increased by 33% over Q1, with the mass exploitation event also driving up instances of CVE/exploits for initial access. Alongside this, Kroll observed other concerning shifts. Our analysis of incidents in Q2 also highlights several areas in which actors have evolved their tactics to bypass common security controls.
Health and wealth under attack
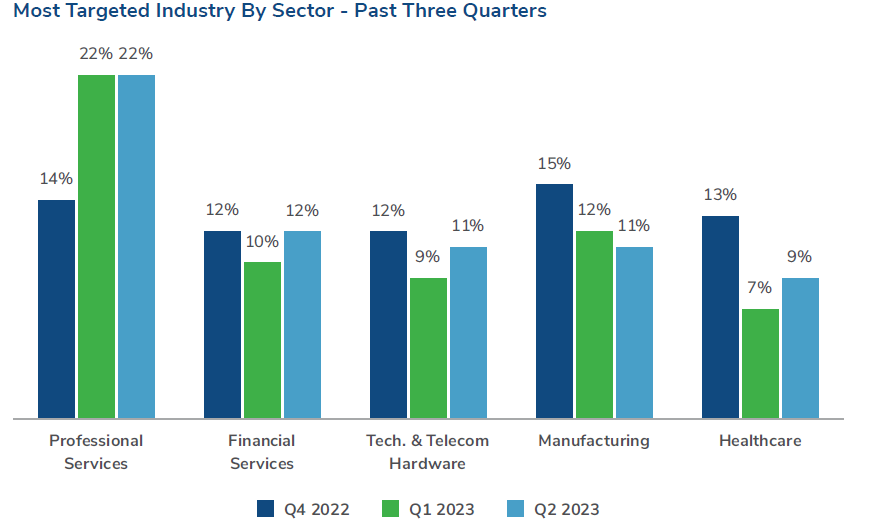
Kroll observed increases in attacks targeting the financial services, healthcare and technology & telecommunications sectors. Attacks on the financial services sector increased by 2%, while attacks on healthcare also grew by 2% – a modest but significant increase which propelled the sector to the top five most targeted industries for the first time in two quarters. The rise in attacks on healthcare aligns with our findings outlined in our Data Breach Report that it was the most breached industry of 2022.
A review of financial services cases identified that the most observed threat incident type was email compromise. While the financial services sector is less frequently targeted by ransomware than other industries, the CLOP group’s ransomware activity impacted small- to mid-sized regional banks.
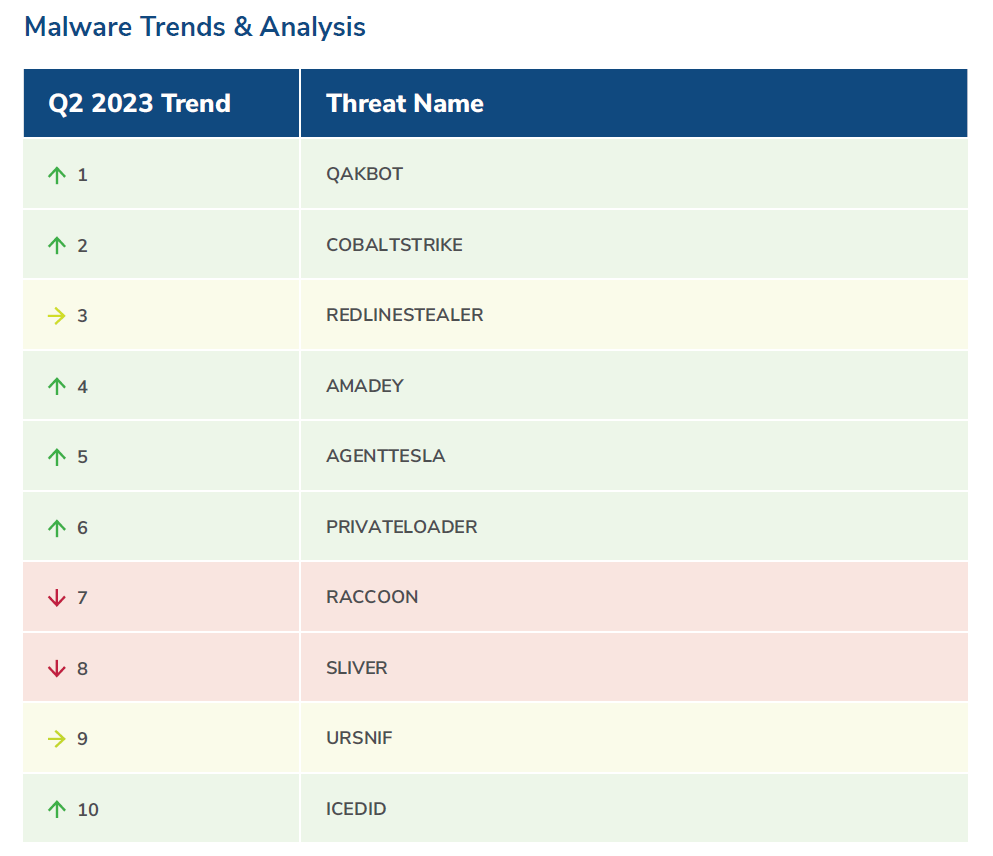
Malware trends & analysis
Kroll actively tracks malware command and control infrastructure, submissions to public sandboxes and active incident response (IR) and managed detection and response (MDR) case data to generate lists of the most active malware strains for comparison.
This quarter, Kroll observed a significant uptick in QAKBOT activity in both casework and from uploads to public sandboxes, matching our knowledge that sizeable malspam campaigns delivering QAKBOT occurred in Q2. Kroll also observed increases in AMADEY and AGENTTESLA. Notably, REDLINESTEALER stays in the top three malware strains detected in both open-source uploads and in Kroll’s own casework.
Threat types continue to evolve
The new report reflects ongoing instability in the threat landscape. Attackers continue to successfully transform and adapt, with our findings highlighting the importance of leveraging continuously updated and reviewed security approaches. Just one example of this type of evolution in Q2 is the use of open redirect abuse in phishing attacks. It is important to note that these types of pivots aren’t only being made in relation to tactics and techniques. They are also being undertaken on an industry level, as seen in the impact of CLOP ransomware activity on regional banks. These changes, alongside continued use of established attack techniques means organisations should ensure that they have a comprehensive cyber security strategy in place.