Redscan has used a Freedom of Information (FOI) request to examine the way organisations operating across financial, legal and general business sectors responded to data breaches in the last financial year. What we’ve found is disappointing but in no way surprising.
Click here to view the report infographic
Timely identification of breaches
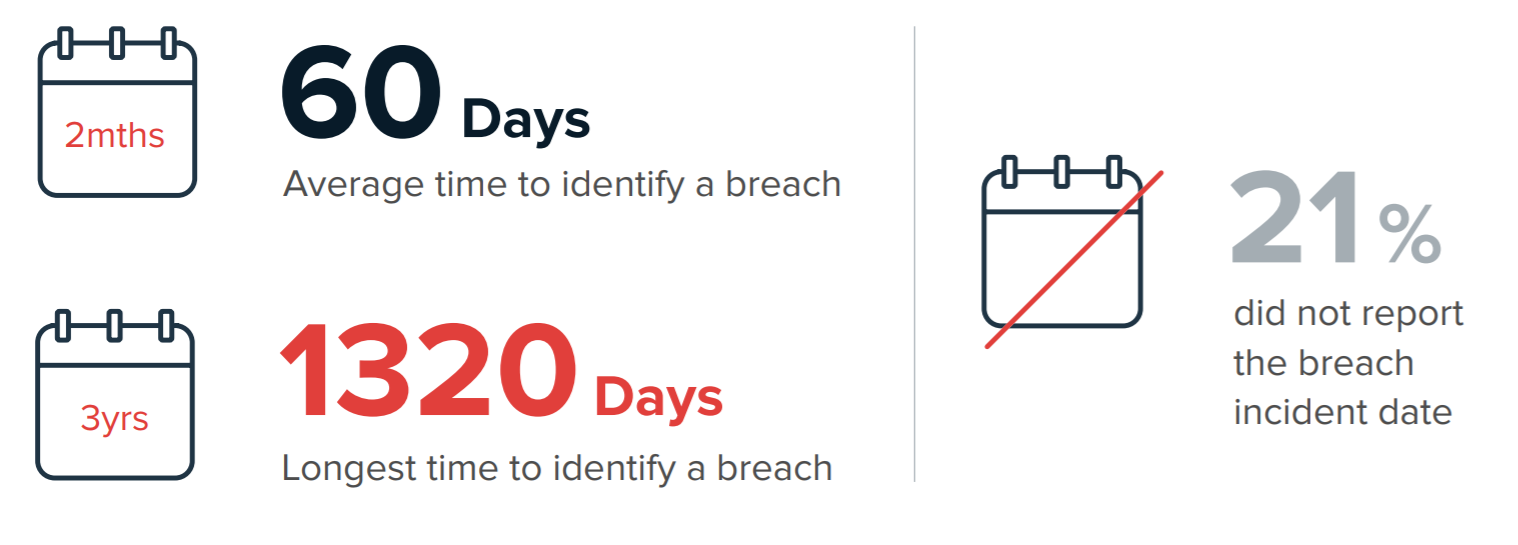
Breaches can’t be reported if they aren’t first identified and recognised, but our research found this is an area where businesses struggled. Across all sectors surveyed, the average time to detect a breach was 60 days. One organisation took over 3.5 years!
The focus of this research was not why one organisation took years to detect a breach. It’s fair to say from our experience, however, that for a variety of reasons, breach detection presents a wide variety of challenges to businesses, which leads to delays.
Thanks to growing cloud adoption and trends such as IoT and BYOD, the attack surface of every business is growing constantly – creating new entry points for attackers to exploit. What’s more, the attackers themselves are using evermore sophisticated techniques to evade detection.
Unfortunately, many organisations lack the specialist technology and expertise needed to detect the latest threats and only realise that this is the case when it is too late – at which point the damage may already have been done.
The cyber security skills gap is a key contributing factor of low breach detection rates. There is currently a national shortage of qualified cyber security professionals, meaning that skilled individuals are at a premium, with organisations often passing cyber security responsibilities to individuals who lack specialised training.
“Data breaches are now an operational reality, but detection and response continue to pose a massive challenge to businesses”, said Mark Nicholls, Redscan Director of Cybersecurity.
“Without the appropriate controls and procedures in place, identifying a breach can be like finding a needle in a haystack. Attacks are getting more and more sophisticated and, in many cases, companies don’t even know they’ve been hit.”
Compliance reporting
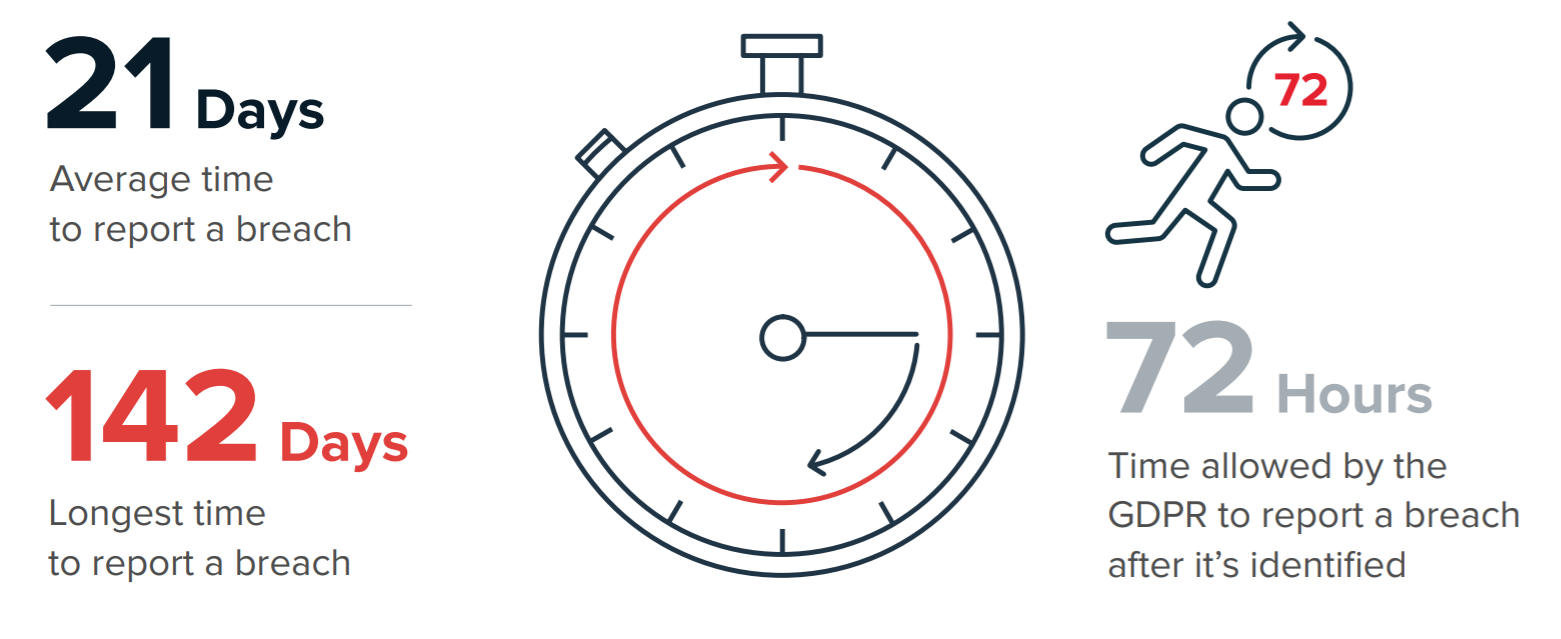
Our research found that the average time taken to report a breach to the ICO post detection was 21 days, while one organisation took as long as 142 days.
The large gap between detection and reporting is undoubtedly a key reason for the introduction of the General Data Protection Regulation (GDPR). Among the requirements of the GDPR is that businesses have appropriate measures in place to detect personal data breaches and report them within 72 hours, with the clock starting the moment an organisation detects a breach.
“It’s incredibly optimistic to think that businesses are better at preventing and detecting data breaches since the introduction of the GDPR,” said Nicholls. “Despite the prospect of a larger penalty, many are still struggling to understand and implement the solutions they need to achieve compliance.”
Our analysis of the FOI data also revealed that more than 9 out of 10 companies did not, when reporting a breach to the ICO, specify the impact of the breach or did not know the impact at the time it was reported. This is another worrying statistic and again suggests that organisations lacked the appropriate expertise and resources to understand the full scope of attacks, such as the type of data and assets compromised. Without this knowledge it is almost impossible to put together an effective incident response plan.
Understanding the impact of breaches has become even more important since the introduction of the GDPR, which says that affected individuals must also be notified of a breach where there is a high risk to their rights and freedoms.
Other trends identified
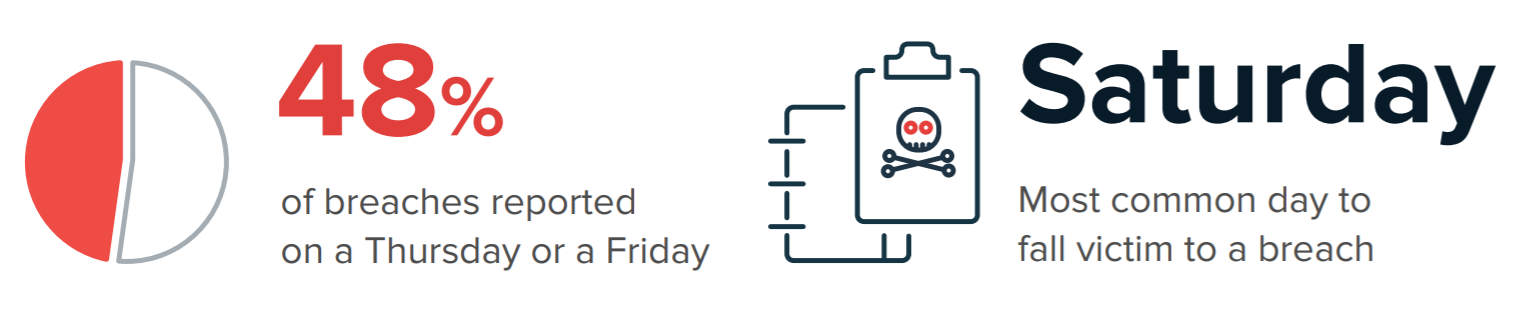
According to our research, Saturday is the day that businesses are most likely to be breached, with over a quarter of breaches that we analysed occurring on this day of the week. This is likely a deliberate tactic by hackers, knowing that IT resources in most organisations are often stretched at weekends.
Meanwhile, Thursday and Friday are the days that breaches were most likely to be reported. Nearly half of reports to the ICO that Redscan analysed were submitted on a Thursday or a Friday, which is a likely demonstration that many businesses are not geared to respond to the round the clock nature of threats.
Mark Nicholls: “Detecting and responding to breaches is now a 24/7 effort. Many organisations lack the technology and expertise they need, which is compounded by a global cybersecurity skills shortage. Resources are stretched even further at weekends, when many IT teams are off-duty – exactly why hackers chose to target businesses out of hours.
“It’s also interesting to note that nearly half of reports to the ICO were submitted on a Thursday or a Friday, good days to bury bad news. This might be overly cynical but I suspect that in many cases, breach disclosure on these days may have a deliberate tactic to minimise negative publicity.”
Performance by sector
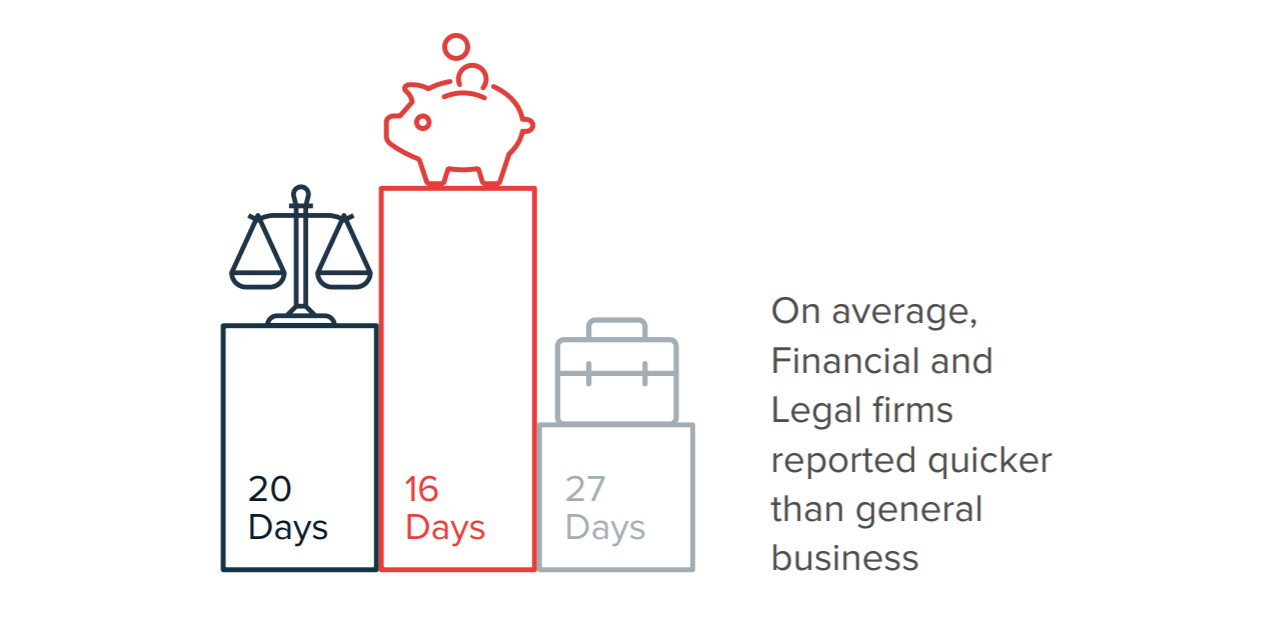
When we analysed the FOI data by sector, organisations in the financial and legal industries reported breaches more promptly than general businesses.
Financial sector firms performed best, averaging 16 days to report a breach, closely followed by legal firms (averaging 20 days), with general business trailing significantly father behind (taking 27 days on average) to report a breach. This is likely to be because of heightened regulatory awareness by financial and legal firms who must also report to their relevant industry body – the Financial Conduct Authority (FCA) or Solicitors Regulatory Authority (SRA).
Mark Nicholls: “In general, firms operating across the financial and legal sectors are among those better prepared to manage data breaches. The fact that even businesses in these high-value sectors were taking two to three weeks to divulge incidents is a key reason why the reporting rules have since been tightened.”
Looking forward
Data breaches are now an operational reality for all business. It’s of the utmost important (not to mention legally mandated) that appropriate controls are in place to detect and respond to them, yet our research shows that immediately before the introduction of the GDPR, firms still had vast improvements to make in order to meet their obligations.
While many businesses, since May 2018, will have become better prepared to respond to breaches than others, swift detection and response is far from universal and continues to pose huge challenges to businesses large and small in all sectors of the economy.
Without appropriate resources in place, businesses will continue to struggle and risk falling foul of their compliance requirements which are now stricter than ever.
Being able to detect and respond to threats in their infancy, before a breach even occurs, is essential and can be achieved through proactive threat monitoring, detection and response. The identification of a potential breach, or a breach in its infancy, can prevent widespread damage and disruption and save organisations from embarrassment, expense and the mitigation required, should a breach occur.
About Redscan
Redscan is an award-winning provider of managed security services, specialising in threat detection and integrated response.
Possessing a deep knowledge of offensive security, Redscan’s experts are among the most qualified in the industry, working as an extension of clients’ in-house resources to expose and address vulnerabilities plus swiftly identify and shut down breaches. Services offered include Managed Detection & Response, CREST-accredited Penetration Testing and Red Team Operations.
By understanding how attackers operate, leveraging cutting-edge threat intelligence, and offering highly acclaimed customer service, Redscan’s cyber security professionals can be trusted to provide the insight and support needed to successfully mitigate information security risk and achieve compliance standards.
Read more:
Security insights from a cyber-aware software development team
Meet Redscan at CRESTCon on 14th March 2019
Cyber incident response – what to do after a data breach




