
5. Veil Evasion
Veil-Evasion generates malicious executables that are not recognised by most of the common anti-virus software. Numerous payload and obfuscation techniques can be applied to a binary, after which the system can then check that no anti-virus vendors on www.virustotal.com have seen the malware hashes previously. The tool doesn’t guarantee files won’t be detected by anti-virus software, but it’s useful if you need to quickly generate a Trojan to bypass an anti-virus, without resorting to writing a Trojan from scratch.
4. PowerSploit
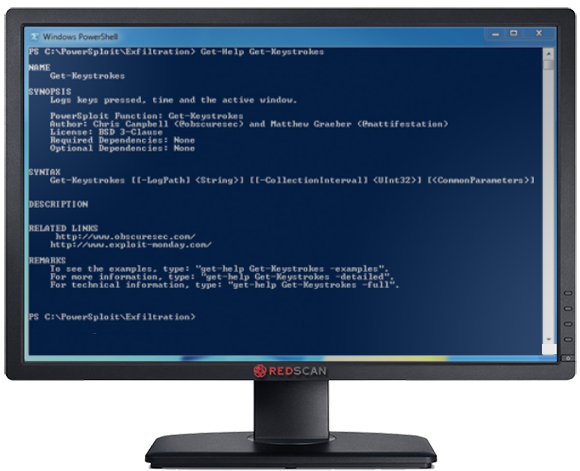
PowerSpolit is a set of PowerShell scripts for use in post exploitation. Since the majority of Windows systems found on corporate networks support PowerShell, using this scripting language is a good fit for most post exploitation tasks, and has the added benefit of evading most common anti-virus software. Scripts included have the ability to capture credentials, perform persistence tasks and execute code directly in memory without touching the disk.
3. Immunity Debugger
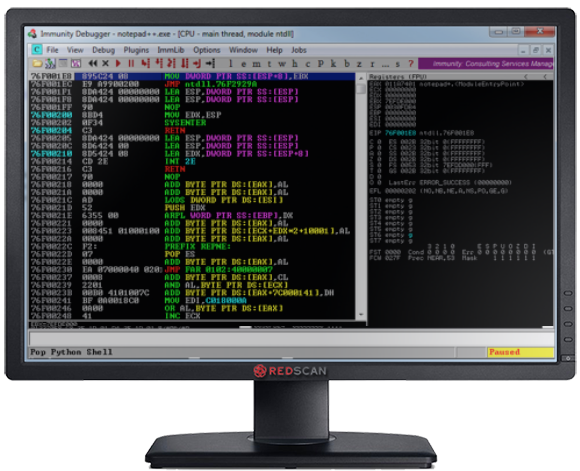
Immunity debugger is a debugger specifically written to assist in writing exploits, and performing reverse engineering of binaries. Support for Python scripting allows for using community written scripts such as Mona.py from Corelan to automate a lot of tasks which previously had to be done manually. When writing exploits for Windows systems, this should be an essential part of your toolkit.
2. BurpSuite
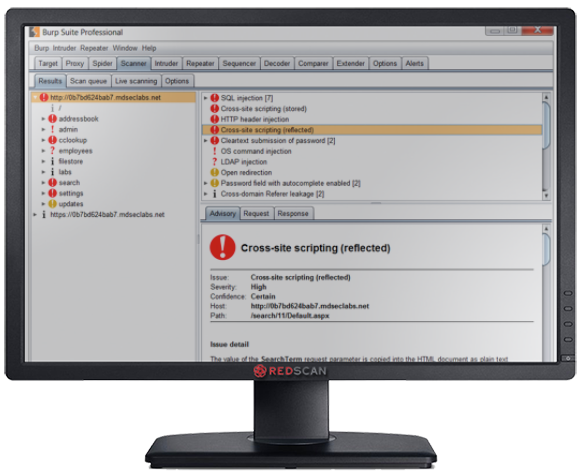
BurpSuite is an integrated platform for performing web application hacking. A free version is provided, however the professional edition includes a number of features making it well worth the asking price. These include an advanced web application scanner for detecting numerous types of web based vulnerabilities. The tool is frequently updated with new features such as the recently added Burp Collaborator system, which allows testing for vulnerabilities which arise from the interaction of remote external systems. Burp’s capabilities can be extended through user extensions, many of which are available for free in the Burp App Store.
1. Kali Linux

Kali is a Linux distribution which comes preinstalled with a number of security tools for penetration testing. Common penetration testing tools such as Nmap, Metasploit and SQLMap are included meaning there is no need to spend hours installing all required tools separately. Kali’s kernel is compiled with support with Radio Frequency Monitoring Mode (RFMON), which makes it a great platform for performing wireless attacks using tools such as aircrack-ng. Strong community support, great price (free) and a large number of tools for different test scenarios makes Kali our penetration testing tool of choice.



