Phishing, the practice of using fraudulent communications to gain access to data and systems, has evolved rapidly over recent years.
Attacks are becoming more sophisticated, and whilst badly written mailshots advising of non-existent lottery wins are still around, the current trend is for sophisticated attacks that closely mirror the presentation and business practices of well-known organisations. Essentially, it’s a number’s game, with the highest rewards going to those who are best able to craft a convincing message.
Big business and government are often used as facades. Their regular schedule of renewals and reminders, and authority grounded in reputation (and sometimes law) are both things phishing attacks attempts to subvert. Within this arena in the UK, there is no bigger fish [pun intended] than HMRC, the government branch responsible for collecting taxes. Attacks that use HMRC’s branding are likely to be developed around themes such as filing self-assessments, late payments and rebates, particularly as we approach and move past the 31st January deadline for tax returns.
20,750 – the number of spoof websites taken down by HMRC in the last year.
Several factors play a part in the relative success of phishing attacks that mimic HMRC’s branding, and it really comes down to the government unwittingly providing all the information criminals need to get started.
Our Red Teaming consultants outline the key factors that boost criminals’ success when creating HMRC related phishing emails.
Accessible style
One of the factors that often lowers the success rate of a phishing attack is errors and discrepancies in the style and presentation of communications. However, in the case of HMRC, the government has publicly made available its complete style guide and has even published a blog about use of fonts, taking the guesswork out of spoofing emails and websites.
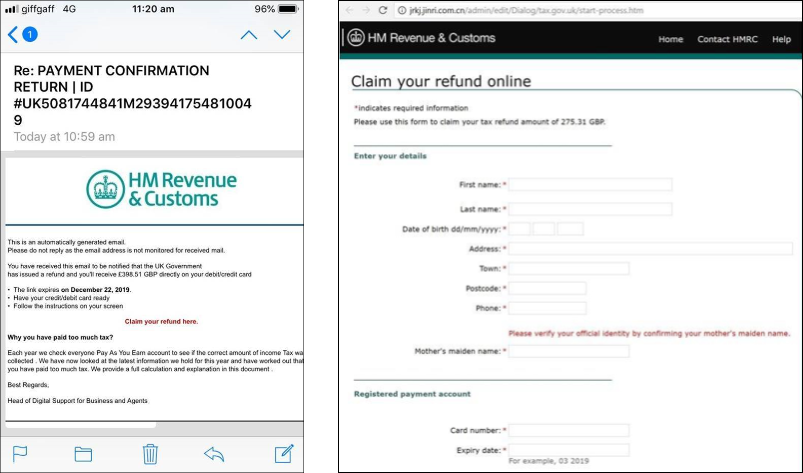
A recognisable and respected organisation
HMRC only sends letters, never emails. If everyone knew that, all the email attacks based on their attacks would fail. As people don’t, the same sense of apprehension that comes with opening an HMRC letter is applied to a scam email. People are fearful of HMRC’s powers, and this triggers a rapid response which makes the public more likely to click a link that purports to be from them. Every adult in the UK has some reason to receive a genuine HMRC letter, making attacks across the broadest possible set of targets a valid tactic, further improving the likelihood of an attack being successful.
Public mistakes
It’s a fair assessment to say another major factor in the success of phishing campaigns that impersonate HMRC is the fact that genuine errors, like the recent early fining of tax-payers for missing a future deadline, adds an interesting element to the way victims interpret their communications. Because the organisation is known to make mistakes, little errors or inconsistencies that might otherwise be viewed cautiously are often viewed as being “normal”, so a victim’s ability to detect an attack in lowered.
Learn lessons the easy way
Research shows that the next wave of phishing attacks that use public sector branding may well be Brexit themed, and as cyber criminals are innovating and learning from events on a regular basis, maybe it’s time to ask if your organisation is sufficiently ready to face these threats.
The good news is that most people who fall victim to phishing attacks learn from their mistakes. But it’s an expensive lesson to learn, can sink a small business and leave individuals thousands of pounds out of pocket. Thankfully there’s an easier way to learn these lessons.
A simulated phishing assessment, performed by Redscan’s experienced ethical hackers, is a great way to test the effectiveness and resilience of in-place controls and procedures designed to detect phishing attacks and help educate users about the dangers. Redscan’s social engineering service provides feedback on the effectiveness of current controls plus training suggestions that can help turn everyone into a threat detector.
Read more:
Securing electronic communications in line with the PECR
10 ways to strengthen your organisation’s cyber security in 2019
Redscan reveals a large disparity in cybersecurity skills and spending across NHS



