Trusts reporting fewer data breaches and employing more qualified cyber security professionals.
The scale of the challenge facing the healthcare sector, even before COVID-19, was significant. In 2020, it became even more pressing with constant reports of critical infrastructure being targeted by cybercriminals.
To understand the unique challenges within the NHS, we submitted a Freedom of Information (FOI) request to every trust in the UK.* The results, when compared with those in relation to a previous request in 2018, suggest improvements in cyber security across the NHS.
Key Findings
- On average, NHS trusts reported two breaches to the Information Commissioner’s Office (ICO) in 2020, down from 2.5 in 2019
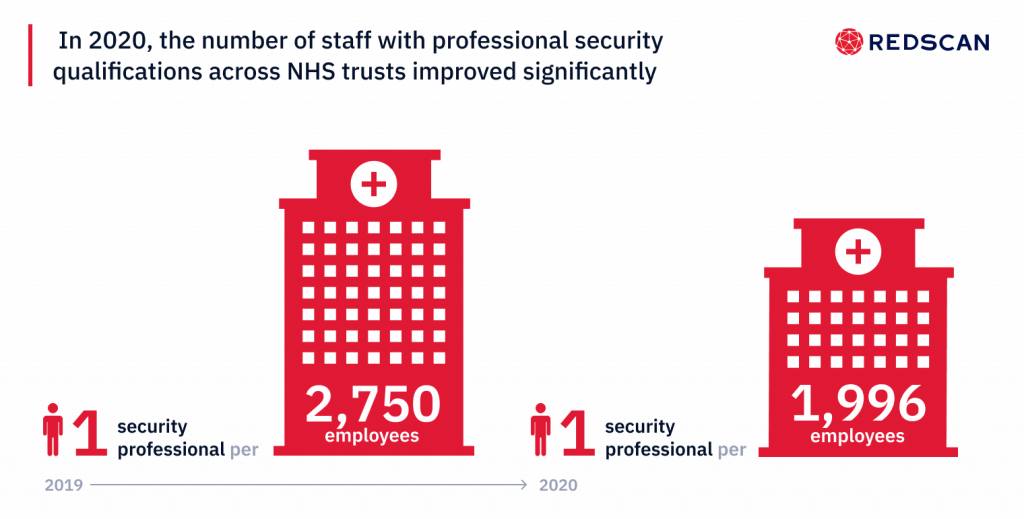
- On average, trusts now have nearly twice as many employees (47%) with professional IT security qualifications (2.8 per trust in 2020 vs 1.9 in 2018)
- One in four trusts had no qualified IT security professionals in 2018 (23%), a figure which has now fallen to just one in seven (15%)
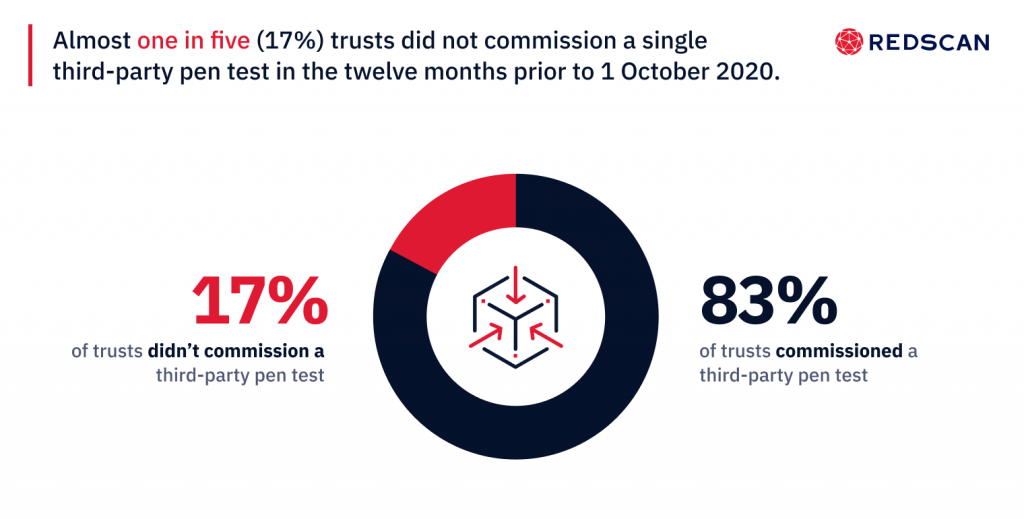
- 83% of NHS trusts commissioned at least one penetration test from an external third-party in 2020
Fewer breaches reported by trusts
In conducting our latest FOI investigation, we wanted to understand how many data breaches were reported by NHS trusts to the ICO in 2020 and compare this figure to previous years. We were keen to avoid contacting NHS trusts during the height of the COVID-19 pandemic, so we made our FOI requests in October 2020 when COVID-19 cases were at a lower level.
Our figures show that, on average, NHS Trusts reported fewer data breaches in 2020 (2.5) than they did in 2019 (2). While at face value, this is encouraging, it should also be noted that more than two thirds of trusts reported the same number or even more breaches in 2020 than they did in 2019.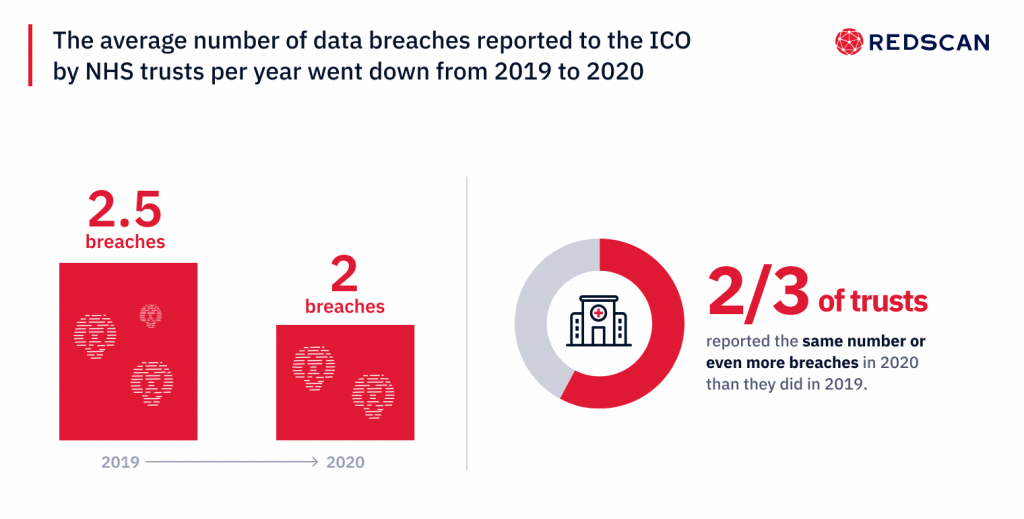
What we say
“Trusts reporting fewer breaches on average to the ICO in 2020 is positive news. However, there is still no room for complacency. Providers of critical infrastructure have been heavily targeted throughout the COVID-19 pandemic and detecting the latest threats can be extremely challenging.
As we’ve seen over the last few years, even the best-resourced organisations can be compromised by cybercriminals. To minimise damage and disruption, having the capability to swiftly identify and respond to attacks is imperative.”
More qualified security professionals in the NHS
The shortage of cyber security skills is a problem for organisations across all sectors, including healthcare, but the NHS appears to have closed the skills gap in recent years. In 2018, we found that, on average, trusts had just one member of staff with professional security credentials per 2,750 employees. In 2020, this number improved significantly to one per 1,996.
Meanwhile, there are also fewer trusts with no qualified security personnel at all. In 2018, this was the case for nearly a quarter of trusts (23%) but this figure now stands at 15%.
What we say
“In addition to technology and processes, people are fundamental to achieving a robust cyber security posture. In 2018, one in four trusts employed no qualified cyber security professionals. This has increased to one in seven.
“Today, there are now more qualified security professionals in the NHS – one for every 1,996 employees on average. A sign of the increased importance being attached to cyber security in the healthcare sector.”
Disparities in training spend
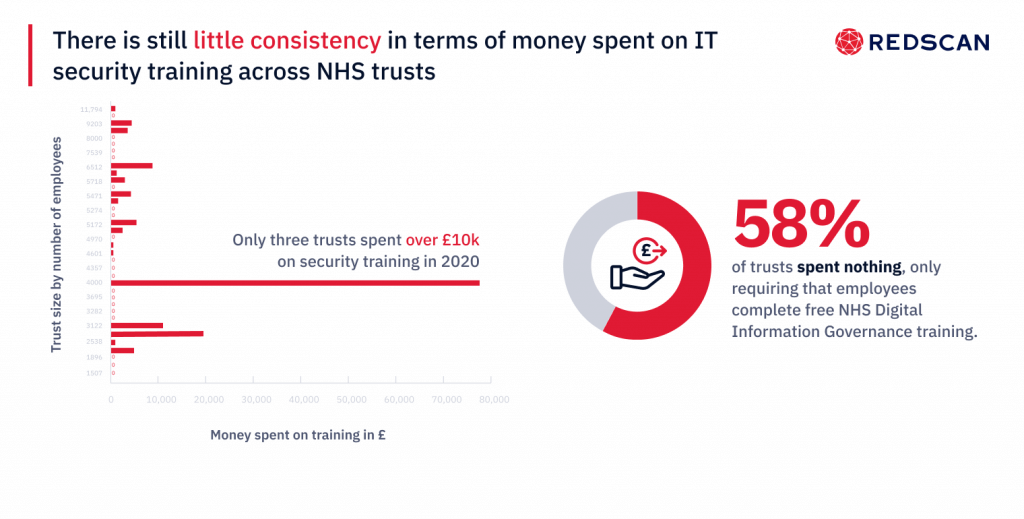
As was the case in 2018, there is still little consistency in terms of money spent on IT security training across NHS trusts. For example, while one trust spent £78k on security training in 2020, more than half of respondents (58%) spent nothing, only requiring that employees complete free NHS Digital Information Governance training.
What we say
“It is positive that digital information governance training is mandatory across the NHS. However, with cyber security threats ever-evolving, it’s also important that trusts provide staff with extra training where necessary. This includes specialist training for cyber security staff plus general awareness sessions for the rest of the workforce.
“It’s interesting to see that disparities in training spend still exist and that spend doesn’t necessarily correlate with trust size.”
Infrequent independent penetration testing
It is highly recommended that all organisations commission regular penetration testing from external third parties to help keep on top of security vulnerabilities. Our research reveals over 80% of NHS trusts that responded to our FOI had at least one independent penetration test carried out in 2020. The average rate was 1.26 tests per trust during this period.
Almost one in five (17%) of trusts did not commission a single third-party pen test in the twelve months prior to 1 October 2020.
What we say
“Even though most trusts are commissioning annual penetration tests from third parties, this may not be enough considering the size of their attack surface and use of specialist equipment. Independent assessments are important to identify risks than can easily be overlooked.
“The NHS Data Security and Protection Toolkit mandates that all organisations undertake a penetration test at least once a year. However, this should be treated as a minimum standard and organisations are encouraged to undertake testing more frequently.”
Conclusion
“In 2018, our FOI revealed a large disparity in cyber security skills and training spend across the NHS. Fast-forward two years, and our latest report provides a valuable snapshot of how the situation has changed. It suggests that while disparities in training spend and penetration testing still exist, trusts are more likely to have qualified security professionals on staff and are also reporting fewer breaches compared to 2019.
“With more and more healthcare organisations being targeted by attackers, every NHS trust needs to ensure it is prepared for the challenges ahead. To deliver an effective service, organisations must continuously improve their defences to protect the patient data and infrastructure they rely on to save lives.”
*Notes
Responses from 64/225 trusts were received between 8 October 2020 and 4 February 2021. Redscan opted to submit its FOI requests on 5 October 2020 when COVID-19 cases were far lower than current levels, requesting data from the last 12 months in relation to security spending, penetration tests, employee training and security credentials. The number of data breaches reported to the ICO only covers part of last calendar year (January 2020-October 2020) and is compared to the same period in 2019. Due to the pressures of COVID-19, many trusts were slower to respond to the FOI or unable to do so. As such, this release is intended to offer an update and point of comparison to results from 2018.
Disclaimer
The information provided in this report by Redscan Cyber Security Limited is for general information purposes only. All information is provided in good faith, however we make no representation or warranty of any kind, express or implied, regarding the accuracy, adequacy, validity, reliability, availability or completeness of any information.




