Kroll’s latest threat landscape report shows ransomware groups increasingly gaining initial access through external remote services.
Q4 2023 presented a complex security landscape with a mix of both positive and negative trends
On the one hand, activity associated with larger ransomware-as-a-service (RaaS) operations, such as LOCKBIT and BLACKCAT, declined due to the success of major takedown operations.
However, negative patterns also continued, like the ongoing focus of threat actors on the professional services industry.
These, as well as other notable trends from the previous quarter, are discussed in the report, Q4 2023 Cyber Threat Landscape Report: Threat Actors Breach the Outer Limits
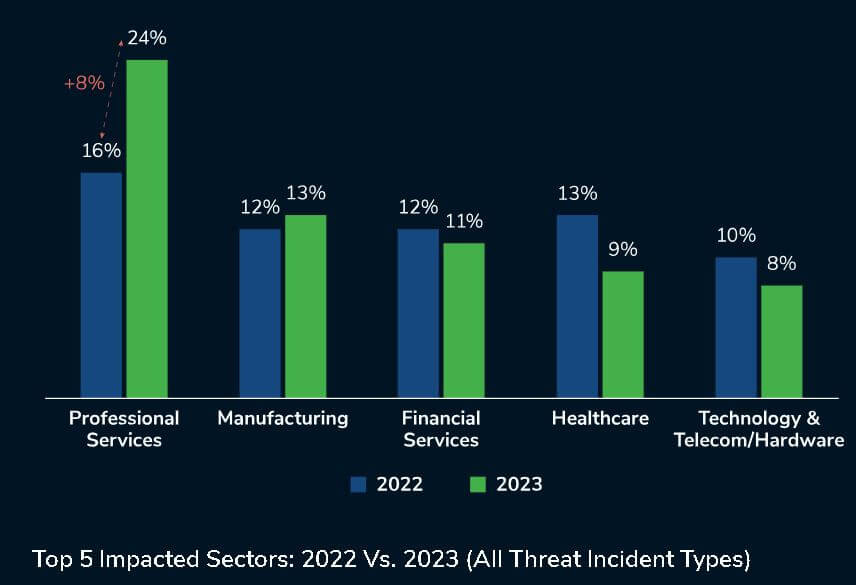
Attackers continue to focus on professional services
In Q4 2023, Kroll observed that attackers focused heavily on the professional services industry, with slight increases also seen in the healthcare sector, particularly in respect to ransomware activity. The focus on the professional services industry is the continuation of a trend noted throughout 2023 and follows a sharp increase in cases impacting the sector from 2022 to 2023.
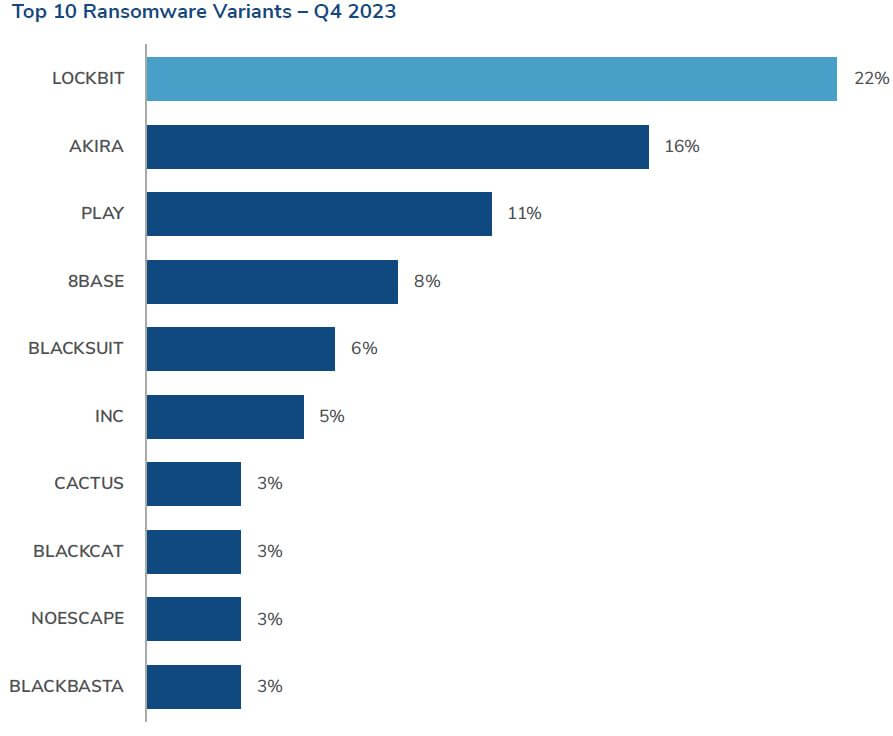
Ransomware groups remain active
Q4 saw activity from a wide range of ransomware groups, with some key players continuing with campaigns observed earlier in 2023. Kroll observed declines in activity associated with larger RaaS operations such as LOCKBIT and BLACKCAT. Following an extremely active Q3, BLACKCAT made headlines multiple times during Q4. To date, the “new” BLACKCAT site continues to post victims.
Kroll also observed upticks in activity by several variants, including AKIRA, PLAY, INC and CACTUS, during Q4. Looking at ransomware cases, the most likely initial access method was external remote services, presenting another key area of concern for organisations.
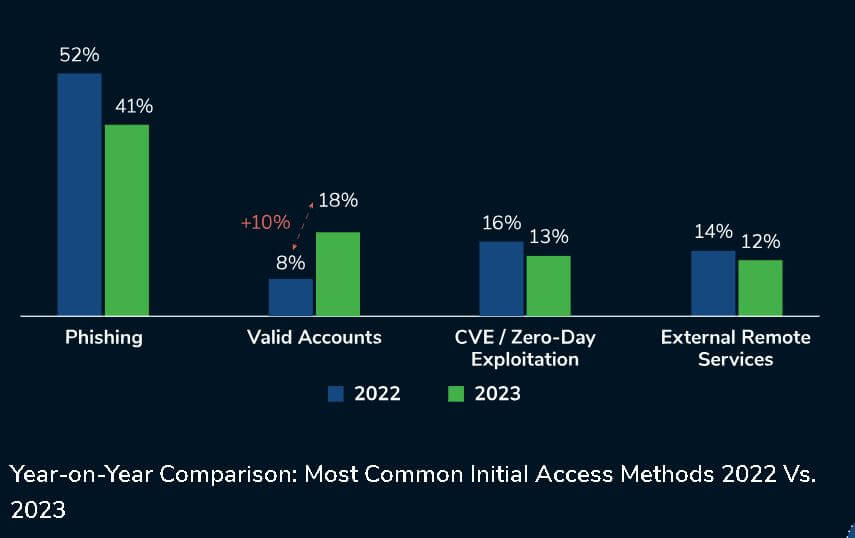
External remote services yield initial access
Although lower in volume than in Q3, phishing continued to be the most likely initial access vector for Kroll engagements. Phishing continues to evolve as threat actors try new and more sophisticated ways to tempt users into clicking on their malicious links. In Q4, Kroll analysts reported on a rise in the use of QR codes in phishing campaigns. These types of tactics make defence more challenging as users may be less likely to perceive these codes as being suspicious, increasing the possibility of them accessing the links via personal devices, which are outside of corporate security monitoring.
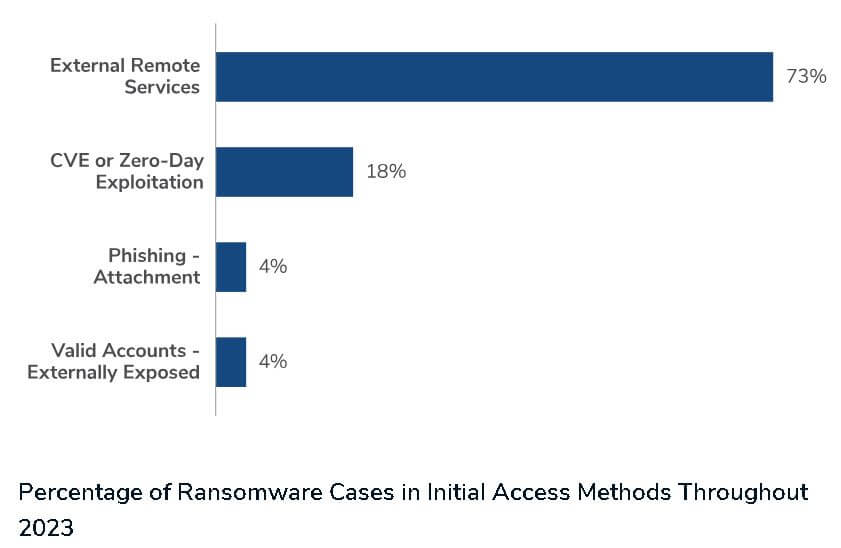
Rise in ransomware cases in initial access methods
Kroll also observed an increase in external remote services used for initial access, particularly by ransomware actors. Kroll identified that, in most cases, actors are either exploiting a known vulnerability, such as CitrixBleed (CVE-2023-4966), or accessing a VPN that lacks multi-factor authentication (MFA) through valid credentials or brute-force attacks. Valid credentials may be obtained in a variety of ways, such as through dark web markets that sell data harvested from information-stealing malware.
The malware and ransomware landscape changes significantly
Q4 saw some dramatic changes to the malware and ransomware landscape, with many being a direct result of law enforcement activity to disrupt and degrade the infrastructure of some of the most prolific adversary groups. In August, the QAKBOT botnet was heavily disrupted, leading to infrastructure changes and a significant drop in QAKBOT infections in Q3. However, the attempts of threat actors to rebuild the botnet put it firmly back in the top 10 list in Q4. In yet another twist to the tale, although QAKBOT is featured high up on our quarterly trend list, we did not observe any successful infections.
Notably, the threat actor tracked by Kroll as KTA248 (TA577, TR), as well as one of the actors operating huge QAKBOT campaigns, began deploying new malware strains to gain initial access into corporate environments. This meant that while in Q3 we saw significant increases in DARKGATE, PIKABOT tops our list for Q4. Both malware strains are operated by KTA248 as a potential successor to QAKBOT. Kroll observed a significant overlap between PIKABOT and QAKBOT infrastructure from early- to mid-2023. In November, Kroll noted a reply-chain phishing campaign delivering PIKABOT.
Infostealers also make up more of the quarterly top 10 in Q4, with LUMMASTEALER (LUMMAC2) and STEALC seeing significant upticks. Throughout 2023, and especially in Q4, Kroll witnessed significant increases in infostealer activity, the development of capabilities and new entrants to the market.
After causing significant harm in 2023 with activity such as leveraging victims’ VPN for initial access via external remote services, LOCKBIT was taken down in Q4. However, the group has since returned to the dark web.
A challenging year lies ahead
The increased use of external remote services by ransomware groups and the advance of other types of threats, such as infostealer malware, highlights that there is no area of security about which organisations can afford to be complacent. Those taking action now will be more likely to achieve the level of cyber maturity required to meet the security challenges of 2024.




