Confidential data is a key focus for cyber-attackers, with health and social care organisations a popular target.
To help secure sensitive data, emails that include health and care information sent to and from health and social care organisations are required to meet the Secure Email Standard (DCB1596). In this article, we discuss the standard, what it covers, and how to ensure your organisation fully meets its requirements.
Health and social care under attack
Health and social care organisations are at significant risk, with over half of UK health and social care organisations falling victim to cyber-attacks, according to research undertaken in 2023. The large volumes of sensitive data held, managed and shared across the sector is the likely reason for this. The Kroll Data Breach Outlook identified healthcare as the most breached industry of 2022, with Kroll observing that this trend has remained steady, a pattern that has been demonstrated again in the new Kroll report, The State of Cyber Defense: Diagnosing Cyber Threats in Healthcare.
What is the secure email standard (DCB1596)?
All emails that include health and care information sent to and from health and social care organisations are required to meet the secure email standard (DCB1596), if the organisation does not use NHSmail. The information standard is published under section 250 of the Health and Social Care Act 2012.
The secure email standard sets out the minimum requirements for a secure email service. Meeting the secure email standard means that an organisation’s email system is secure enough to keep sensitive information safe. This covers the storage and transmission of email, including where email is used for the sharing of patient identifiable data. The standard includes:
- The information security of the email service
- Transfer of sensitive information over insecure email
- Access from the internet or mobile devices
- Exchange of information outside the boundaries of the secure standard
How to comply with the secure email standard
Organisations can meet the requirements of the secure email standard in one of two ways:
1. By implementing an already compliant service such as NHSmail, Office 365 or Google Workspace for all staff
For these services, requirements include ensuring there is a process in place to notify the NHSmail team on becoming aware of any breach of security, setting policies and procedures for the use of secure email using mobile devices, and complying with DCB0160: Clinical Risk Management: its Application in the Deployment and Use of Health IT Systems. It also includes the requirement to establish policies and procedures for staff using the secure email service to ensure that they understand how to utilise it appropriately and safely. Each organisation is responsible for verifying their own configuration. To support this, NHS Digital a Center for Internet Security (CIS) Microsoft Office 365 foundation benchmark assessment Level 2 criteria that they assess against for compliance.
Organisations can show they are meeting the standard by completing an IT health check (ITHC), or penetration test, using the scope and CIS Microsoft 365 Foundation Benchmark Testing Results and Corrective Action Plan template. Each organisation should define any mitigation or remedial action plans and submit them to NHS Digital Secure email standard service for approval. More guidance is available in the CIS Microsoft 365 Foundation Benchmark Testing Results and Corrective Action Plan template.
The Microsoft Office 365: Secure email configuration guide has been co-produced with Microsoft, allowing instances of O365 to be enabled to securely route emails to and from NHSmail.
Google workspace: Secure email configuration guide has been co-produced with Google, allowing instances of Workspace to be enabled to securely route emails to and from NHSmail.
As well as completing the organisation section of the standard, organisations hosting their own email services must submit assertions and evidence that they meet the ICT Service Provider elements.
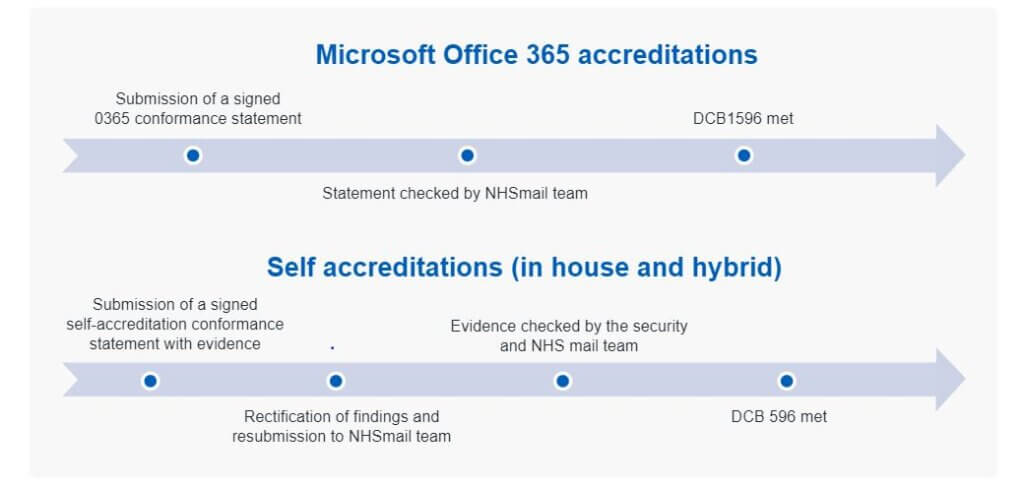
2. By demonstrating that their own service is compliant with the secure email standard by following the secure email accreditation process
The secure email end-to-end accreditation process involves:
- Submitting a signed self-accreditation statement, with evidence
- Evidence being checked by the NHS Digital Data Security Centre and NHSmail team
- Issues rectified and the statement resubmitted to the NHSmail team
- DCB1596 met
The templates eligible for accrediting an email service and that should be returned with the required evidence are:
- DCB1596 Google Workspace Conformance Template
- DCB1596 Microsoft Office 365 Conformance Template
- DCB1596 Self Accreditation Conformance Template
- DCB1596 ICT Service Provider Template
The accreditation process
Accreditations for the Secure Email Standard are valid for one year, with organisations required to contact feedback@nhs.net with updated accreditation evidence ahead of the expiry date. Organisations failing to re-accredit by the expiry date are removed from the secure email web page. The duration of the accreditation period is defined by the resources of the accrediting organisation and their ability to provide all the required documentation.
How Kroll can help
Kroll is uniquely positioned to enable organisations to safeguard their confidential and sensitive data. Kroll has helped hundreds of healthcare organisations test their IT and OT infrastructure, enhance their information security program, monitor and detect threats, respond to incidents and notify impacted populations in the event of a data breach.
Our field-proven cyber security assessment and testing solutions help identify, evaluate and prioritise risks to people, data, operations and technologies worldwide. We offer advice on policies and procedures to human factor influences and technical controls for every data touchpoint in your organisation. As part of this, we deliver Microsoft 365 security assessments that are directly informed by insights gained through our status as the world’s No. 1 incident response provider and our experience of investigating Microsoft 365 security incidents of all sizes, types and complexities.
Learn more about our cyber security solutions for healthcare




