Overview
Extracting security insight from raw threat data
Sourcing, aggregating and analysing the latest cyber threat intelligence can be complex, time-consuming and resource-intensive. Redscan’s security operations centre team of analysts, engineers and researchers are highly experienced working with threat intelligence from a range of sources and drawing actionable insight from it to improve the security of our clients.
Sources
Sources of threat intelligence
Value
The value of cyberoffensive intelligence
Threat intelligence from Redscan Labs and offensive security engagements conducted by our red team means that our security experts are always led by a deep level of cyberoffensive intelligence. Staying-up-to-date with the latest tactics and techniques of adversaries ensures that we are better placed to defend our clients against them.
Offensive security intelligence helps our teams to improve their awareness of the latest security vulnerabilities, detect attacks earlier in the kill chain, and respond to incidents more swiftly and effectively.
Application
How we apply threat intelligence to better protect your business
Redscan’s SOC team use the latest external and in-house intelligence to:
- Enhance situational awareness and decision-making
- Conduct proactive threat detection
- Improve alert analysis and triage procedures
- Automate incident response actions
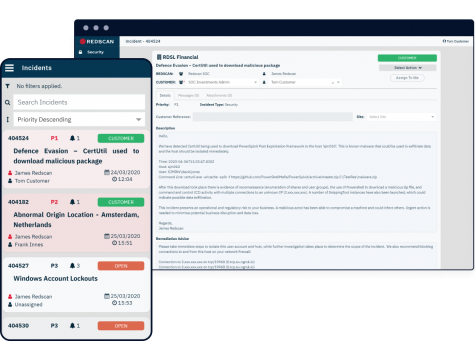
CyberOps
Supplying actionable security insight and intelligence through one unified platform
CyberOps, Redscan’s proprietary Threat Management Platform, is the virtual interface between our Cyber Security Operations Centre (CSOC) and customers of our managed security services. CyberOps’ alert correlation and enrichment engine harnesses the latest threat intelligence to add greater context to security alerts and help better distinguish genuine incidents from false positives.
Redscan Labs
Enhanced threat visibility with Redscan Labs
Redscan Labs is a specialist division within Redscan’s cyber security operations centre (CSOC). By closely monitoring the security landscape to identify new indicators of compromise (IOCs) and the latest tactics, techniques and procedures (TTPs) of threat actors, our in-house team of researchers ensure that our red and blue security teams are always guided by the highest quality cyber threat intelligence.
Get in touch
Complete the form for a prompt response from our team.

Resources



