Having the capability to analyse network traffic for the presence of malware and other malicious activity is essential to help your organisation swiftly detect and respond to criminal attempts to steal sensitive data.
Once malware infects a system, it typically communicates back to its Command and Control (C2) server to receive further instructions, which often involves data exfiltration. In this latest Redscan Labs article, we examine six common approaches used by attackers to steal data and the methods organisations can use to identify them.
1. Traffic Obfuscation
Using penetration testing tools such as Cobalt Strike, it’s possible for an attacker to inject C2 traffic into an existing traffic profile.
The screenshot below shows Wireshark packet sniffer output. At first glance, the traffic appears to be legitimate Google safe browsing traffic, however, upon closer inspection, an encrypted string is inserted at the bottom of the POST request.
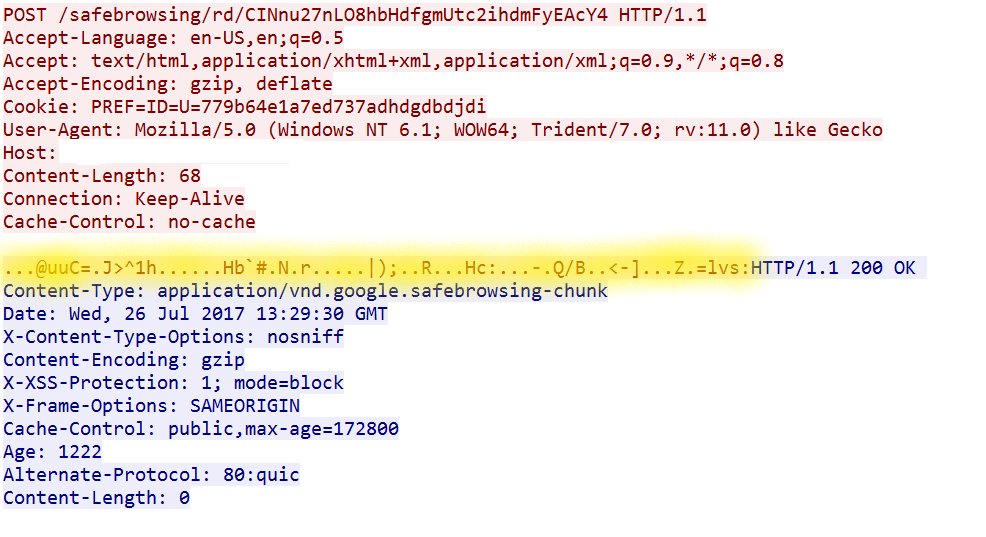
Obfuscated traffic can be detected using a number of methods. One of the best west ways is to search for malicious domains listed on reputation databases such as the AlienVault Open Threat Exchange (OTX).
If specific patterns are gleaned through analysis of code and threat intelligence, Network Intrusion Detection System (NIDS) signatures can be written to proactively detect such sequences.
2. DNS Tunnelling
A lot of people are aware of DNS tunnelling, but a common misconception seems to be that it requires a host to be able to communicate directly outbound over port 53 to the Internet. In reality, malicious DNS traffic will continue along the same path as regular DNS traffic. In most environments, a client’s DNS requests will be forwarded to an internal DNS server before being sent to the Internet.
To detect this type of activity, DNS request logs need to be ingested into a SIEM system for analysis, with large DNS traffic spikes a good indicator of anomalous activity. Analysis of Netflow traffic and characteristics can also help to identify compromises and C2 channel communication.
3. Encrypted Traffic
A common way cybercriminals seek to avoid network intrusion detection systems (NIDS) is to encrypt traffic.
Ingesting proxy logs into a SIEM solution can go some way to identifying this type of communication. Full packet inspection and the use of Endpoint Detection and Response (EDR) tools to identify encrypted communications between endpoints can also be helpful.
Termination of SSL traffic prior to inspection can enable NIDS solutions to better detect and inspect such traffic.
4. Internet Control Message Protocol (ICMP)
Many organisations allow ICMP Echo requests and Echo responses through their firewall as this aides in debugging connectivity issues. This same traffic, however, can also be used by malware to communicate with C2 systems.
Network-based intrusion detection systems can help to identify this type of activity by detecting malformed ICMP traffic. Behavioural analytics, SIEM and EDR can also be used to identify and contextualise unusual behaviours and correlate them with indictors of compromise (IoCs) as well as known attacker tactics, techniques and procedures (TTPs).
5. Domain fronting
Some proxy systems and security solutions detect malicious traffic based on the reputation of the target domain. This is problematic for attackers, as when their domains are marked as malicious, new domains need to be set up.
To get around this problem, attackers can use a content distribution network (CDN) to forward traffic to a backend malicious domain. This typically works by sending HTTP requests to a CDN distribution node, then altering the host header to forward the traffic to a malicious domain.
Analysis of proxy logs can help identify instances of domain fronting within the host header, and if the header points to information in the message body, a full packet capture toolset can help identify and correlate findings with established IOCs.
6. Third party domain usage
To bypass domain reputation-based detection, some recent malware variants have started communicating via social media platforms such as Twitter. This benefits attackers as these platforms have good domain reputations, and their use is likely to be permitted within organisations.
Using a combination of advanced endpoint protection tools, organisations can detect unusual processes and identify and isolate services communicating directly with social media platforms or via browsers in the background.
The importance of proactive network and endpoint monitoring
With attackers becoming increasingly adept at hiding their presence, organisations must be proactive in their approach to security. By utilising a range of network and endpoint monitoring tools, malware-based threats can be identified and eliminated in their infancy – before they have a chance to cause damage and disruption.
ThreatDetect™ is Redscan’s award-winning Managed Detection and Response service. Our CSOC analysts and engineers utilise a range of security technologies, including SIEM, IDS, vulnerability scanning, behavioural analytics and endpoint detection tools, alongside the latest industry intelligence, to help organisations rapidly detect and respond to threats and breaches across cloud and on-premise environments.
The purple team mentality is crucial to Redscan’s approach to cyber security. Redscan Labs, our threat research and analytics division, provides actionable insight and a platform for our red and blue team security professionals to collaborate and improve the effectiveness of our services.
Read more:
Redscan Labs: Businesses urged to remain vigilant about VPNFilter malware
Redscan Labs: Malware unpacking – How to uncover hidden threats
Identifying and tackling distribution fraud



