Colonial Pipeline provides fuel to approximately 45% of the East Coast area of the US.
On Friday, 7th May, the organisation confirmed that a ransomware attack had forced it to shut down all its IT infrastructure – an infection attributed to the DarkSide cybercrime gang.
However, just one week later, amid reports that a ransom of around $5 million had been paid out, DarkSide announced that it had stopped operating entirely. In this blog post, we examine these events and debate whether they have led to the demise of the cybercrime group – one that has risen rapidly up the watch lists of security teams over the last 12 months.
What took place in the Colonial Pipeline ransomware attack?
According to the FBI, an Eastern European cyber gang referred to as DarkSide was able to infiltrate the network of Colonial Pipeline and exfiltrate approximately 100 gigabytes of data in order to obtain leverage over the company.
While pipelines were not physically affected, fuel flows were cut off because the company’s customer billing system was taken offline by the attack.
“We proactively took certain systems offline to contain the threat, which has temporarily halted all pipeline operations, and affected some of our IT systems.”
Colonial Pipeline
The impact of the shutdown was a self-perpetuating cycle of chronic fuel shortages, panic buying, rising fuel prices, and large-scale disruption to businesses and households. This was severe enough for many US states to declare a state of emergency and introduce temporary legislation to enable businesses to cope with the fallout.
The pipeline became operational again on Tuesday 18th May and while the company has been working fast to remediate the damage caused, it will take some time before the fuel supply is operating as usual.
Who is DarkSide?
DarkSide has been in existence since August 2020, when it made its ransomware-as-a-service (RaaS) operation known on hacking forums. It used a high-traffic leak site on the darknet to recruit affiliates.
It also stated that it would only target organisations that it believed could afford to make ransom payment and not target providers of important public services such as hospitals, funeral providers, educational institutions, charities and government departments.
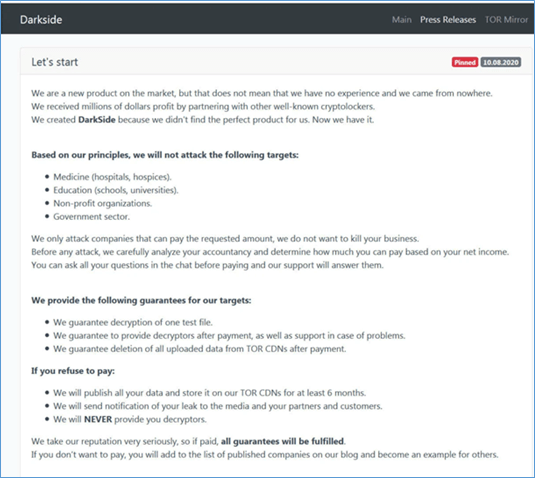
DarkSide Press Site (Source: Kroll Threat Intelligence Team)
How did DarkSide operate?
DarkSide operated a ransomware-as-a-service model, allowing affiliates to purchase the gang’s ransomware, payment portal and other services to conduct attacks. Supplementary resources available to apply additional pressure on victims included:
- The ability to launch Distributed Denial of Service (DDoS) attacks on victims to signal to the outside world that they are undergoing an attack.
- A call centre to harass victims into paying – reports show that victims typically started to receive calls three to five days after initial infection.
- The ability to infect and encrypt Windows and Linux operating systems.
All of these capabilities combined to make DarkSide a serious and intimidating threat, which in turn led to the recruitment of more affiliates – leading to yet more attacks and more profit for the cartel.
Affiliates of DarkSide were required to pass an interview and a test of their skillsets before being permitted access to the operation. This served as a way to maintain operational security and ensure that the affiliates had the skills required to generate more income for the group.
DarkSide’s operations shared similarities with other infamous ransomware gangs such as REvil, GrandCrab and Fin7. The following note delivered to a DarkSide ransom victim, (an example supplied by Kroll’s Threat Intelligence team), is notably similar to the REvil ransom note left on victims’ systems.
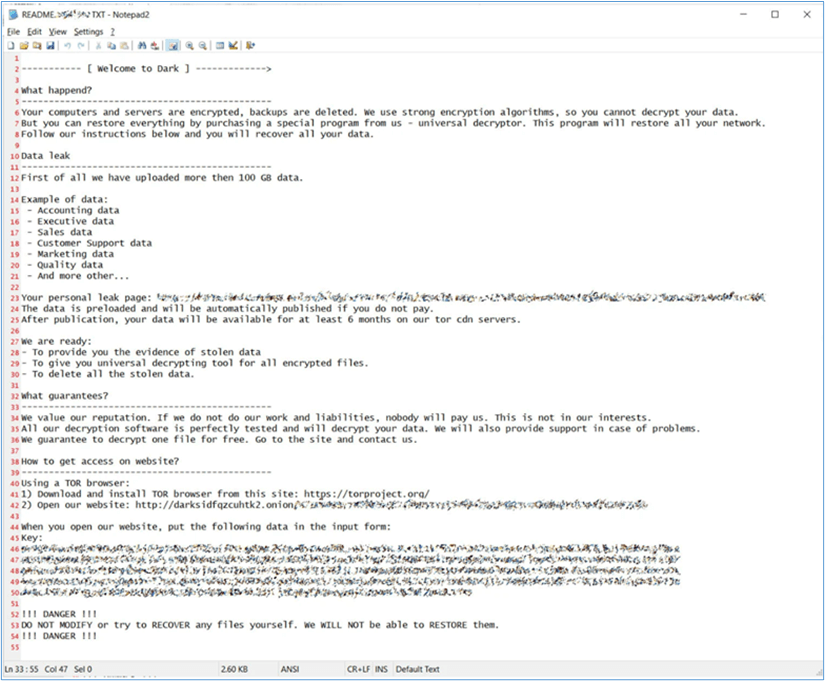
Example of a DarkSide ransom note (Source: Kroll Threat Intelligence Team)
Based on previous DarkSide incidents, the threat actor typically relies on various legitimate open source intelligence (OSINT) tools to facilitate its attacks.
DarkSide actors have previously been observed gaining an initial foothold into the environments of victims through phishing, by exploiting remotely accessible accounts, systems and Virtual Desktop Infrastructure (VDI), as well as by using Remote Desktop Protocol (RDP). They have also been known to use credential dumps found on the dark web to easily gain access to networks.
DarkSide actors have also been observed using RDP to maintain persistence. Threat researchers have observed Darkside ransomware operators navigating to ESXi administration interfaces and disabling snapshot features prior to the ransomware encryptor deployment, which affected several VM images. DarkSide actors primarily used The Onion Router (TOR) for Command and Control (C2) and have also been observed using Cobalt Strike.
How did DarkSide ransomware operators make money?
Several months prior to the attack, researchers observed different versions of DarkSide RaaS being offered on Russian-language forums exploit.in and xss.is. The group had been actively recruiting new affiliates by highlighting the potential for them to earn pay-outs of over $500k.
Cybercriminals have been extensively using Bitcoin and other cryptocurrencies, such as Monero, since they are more difficult to monitor and track by law enforcement authorities. Cryptocurrency also enables cybercriminals to conduct dark web transactions and launder money by using unnamed and privacy-based virtual wallets. Cybercrime on deep and dark web forums is also facilitated by the usage of tumbling and coin-mixing techniques and the lack of official identification documentation and processes when it comes to cryptocurrencies.
In April 2021, prior to the Colonial Pipeline attack, DarkSide announced that it was targeting companies listed on NASDAQ and other stock markets. It indicated that it would be willing to give stock traders information about upcoming leaks, in order to allow them to make potential profits due to stock price drops after an announced breach. Redscan’s Threat Intelligence team believe it is highly likely that ransomware operators such as DarkSide will diversify their sources of income by adding other potential streams of revenue.
How did the Colonial Pipeline attack undermine DarkSide?
In a recent post on its website, DarkSide apologised for the attack on Colonial Pipeline, stating that it was purely seeking financial gain and never intended to disrupt critical national infrastructure. The ransom demand, believed to have been around $5m, is reported to have been paid, but it is interesting to note that this amount is lower than the sums paid out by other organisations that suffered attacks of a similar nature, which would often have generated demands of over $30m.
In its announcement, DarkSide also implied that the attack was the responsibility of one of its affiliates, and not the group itself. This is in breach of DarkSide’s ‘code of conduct’ which strictly prohibits targeting critical infrastructure, probably because of the negative attention that doing so would attract.
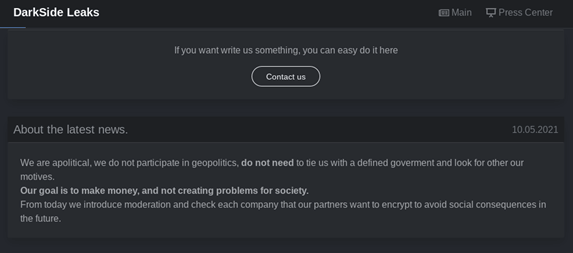
DarkSide leaks site (Source: Kroll Threat Intelligence Team)
The Colonial Pipeline attack earned the DarkSide group and its network a great deal of unwanted attention. By attacking an organisation integral to US infrastructure, it found itself at the centre of both a media and a political storm, with many moves in the background by federal and law enforcement agencies to pursue the group and its affiliates.
The DarkSide customer portal that the group uses to run its criminal activities like a business went down on Thursday 13th May. This was followed by an announcement on the darknet on Friday 14th May that the group was wrapping up all of its operations and ceasing its activities. It also promised to fulfil its financial obligations to its affiliates.
While there has been some speculation that the FBI and other law enforcement agencies took down DarkSide’s infrastructure, there is currently no evidence to support this.
What are the wider effects of the Colonial Pipeline attack?
On the 14th of May, the xss.is forum announced that it was banning posts relating to ransomware. This decision is likely to have been triggered by the high level of disruption caused by the Colonial Pipeline attack and by an attack on the Irish National Health Service by the Conti group.
Since then, posts on Twitter show that DarkSide has given the XSS forum owners 22.1 BTC (Bitcoin), equivalent to approximately $1 million, in order to compensate affiliates who require payment. The processing of these payments has not been confirmed and criminals are still posting claims on the forums.
Another large-scale ransomware group, REvil, has released a statement to say that it will cease attacks on educational institutions, governments and healthcare organisations globally. Threat actor Avaddon announced that it too was adopting a similar policy.
How to protect your organisation against ransomware attacks
The tactics, techniques and procedures (TTPs) and the Indicators of Compromise (IoCs) used by DarkSide are used by other ransomware groups. As we have seen this year, with the demise of the Emotet botnet, cybercrime groups come and go, and we are living in a period of continual disruption and transition.
We recommend that organisations consider the following steps to mitigate the risk of a ransomware infection:
- Identify ransomware behaviour by installing ransomware protection technologies like Endpoint Detection & Response and NextGen AntiVirus. Ransomware can be traced because the malware has observable patterns. Once these are detected, the tools have the ability to help block infections before they spread.
- Back up your systems locally and to the cloud. Should a ransomware virus hit your system, the back-ups will enable you to restore operations.
- Network segregation is important for restricted access to your data. Every organisation should be particularly cautious when granting administrative privileges.
- Keep on top of patch management to ensure all your systems are up-to-date and to minimise vulnerabilities that could be exploited.
- Use Multi-Factor Authentication (MFA) on as many applications as possible. This is especially important for remote login and virtual application services as ransomware groups can easily access these services using stolen or dumped credentials found on the Darknet.
Using DarkSide Threat Intelligence to detect and respond to ransomware
To help detect and respond to the latest ransomware, Redscan has collected over twelve thousand DarkSide Indicators of Compromise (IOCs) from incident response investigations and open source materials to ensure that our clients benefit from the latest telemetry.
As part of our ThreatDetect™ Managed Detection and Response (MDR) service, we continually monitor the TTPs used by DarkSide and other threat actors, to enhance the visibility of the latest cyber threats and rapidly eliminate them.
Find out more about ThreatDetect




