Benefits
The Benefits of Kroll Responder Managed Detection and Response (MDR)
A leading global 24/7 MDR solution
Get in touchHow our MDR service works
The visibility to detect
The context and actions to respond
What Our Customers Say
MDR Service Features
A turnkey solution for threat detection
Kroll Responder provides everything your organisation needs to detect and respond, 24/7.
Coverage
Threat detection and incident
response in the cloud

Security orchestration
High-fidelity telemetry for threat awareness and decision advantage
Kroll Responder’s MDR experts integrate the most valuable security telemetry into your technology stack, benchmarking it against frameworks such as MITRE ATT&CK to minimise visibility blind spots. We enrich this telemetry with frontline threat intelligence to help improve real-time detection of the latest adversarial tactics and techniques.
More about threat intelligence More on MDR use casesCyber threat hunting
Seeking out known and unknown threats at the earliest stages of attack
Using a combination of manual and machine-assisted techniques, we continually search for indicators of compromise, tune security systems to better understand regular network activity, create watchlists and conduct scenario-based testing to validate the effectiveness of controls and processes.
Learn more about our SOC Learn more about threat hunting

events-based response
The security outcomes needed to rapidly respond
Kroll’s SOC analyses and triages all incoming security alerts and, once a genuine incident is identified, provides the actionable mitigation guidance and incident response actions to respond quickly and effectively. We offer remote and on-site support, as well as ‘Events-based Response’ – automated playbooks to contain and disrupt a wide variety of threats.
Learn more about Cyber Incident ResponseChat with an expert
Get in touch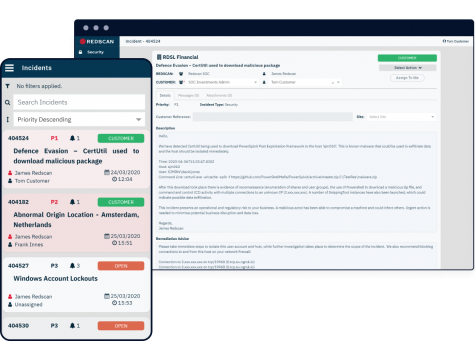
The Redscan Platform
End-to-end threat management, security analytics and reporting
The Redscan Platform™ is the threat management platform used to deliver our Kroll Responder Managed Detection and Response MDR solution. Redscan integrates with all the underlying technologies included as part of the service to enable our SOC team to provide swift and secure incident analysis, actionable mitigation guidance, automated response actions and clear service reporting through a single pane of glass.
Learn more about The Redscan PlatformMDR vs MSSP
MDR vs MSSP - what's the difference?
MSSP services can help organisations deploy a baseline security infrastructure without adding headcount, but these cost avoidance benefits are often offset by providing little value beyond incident alerting and failing to adapt to the changing threat landscape.
True MDR solutions go well beyond this, providing a turnkey service for threat detection, hunting, investigation and response. Utilising telemetry from across the enterprise, MDR solutions should be flexible and scalable, layering telemetry as secuity maturity evolves, while being transparent with detection and response processes.
Learn moreMeet some of our MDR team
Why Kroll?
Your trusted partner for
Managed Detection and Response
- A leading global MDR solution
- Rated 9/10 for overall customer satisfaction
- CREST-accredited Security Operations Centre
- An outcome-focused approach
- Red and blue team security expertise
- Technology agnostic
MDR FAQ
Frequently asked questions
- What is MDR?
-
Managed Detection and Response (MDR) is an advanced security solution that brings together threat detection, response and remediation activities in one solution to help organisations proactively hunt for, investigate, respond to and remediate threats around the clock. By gaining comprehensive visibility of threats through MDR solutions, companies are better able to enhance their security posture and reduce their risk exposure.
View the Kroll MDR Buyer’s Guide for more insight.
- How does MDR work?
-
An effective MDR solution combines the people, processes and technologies required to provide actionable insights and analytics and enable organisations to significantly strengthen their security posture. This supports greater incident awareness and faster, more reliable decision-making. A good MDR solution will apply a structured approach that should cover ingestion, analytics, investigation and response.
- What does MDR include?
-
An effective MDR service brings together many key security elements. It is defined by aspects such as real-world cyberoffensive intelligence, high-quality detection tools and experienced Security Operations Centre (SOC) experts who can act as an extension of an organisation’s team. Other key elements of a high-quality MDR service should include the integration of network and endpoint telemetry from a wide range of log sources, scenario-based testing to simulate potential attacks, and integrated incident response.
- How long does it take to implement a Managed Detection and Response service?
-
The length of time it takes to implement an MDR service varies according to an organisation’s scope, size and requirements. Rather than being defined by their underlying technologies, MDR services offer a turnkey approach built around defined outcomes and goals to address specific security use cases. This means they can be deployed in weeks instead of months, greatly reducing time to value.
- How does MDR facilitate regulatory compliance?
-
Taking a more proactive approach to threat detection is now an important element of achieving compliance with the latest regulations and standards. By providing this type of insight and detailed reporting, MDR solutions help organisations to meet monitoring requirements and standards, including those within the GDPR, the Data Protection Act 2018, the Directive on the Security of Networks and Information Systems (NIS Directive or Cyber Security Directive), Payment Card Industry Data Security Standards (PCI DSS) and more.
- What does a Managed Detection and Response service cost?
-
MDR solutions are significantly more affordable than the equivalent costs of setting up an in-house SOC. Because it removes the requirement to recruit a team of security specialists, deploy and manage a wide range of technologies and run a 24/7 monitoring operation, MDR offers organisations significant financial savings. The cost of an annual MDR solution subscription will be defined by aspects such as the type and number of technologies being deployed and the number of network assets and endpoints being monitored.
Get started with our MDR service
Shut down threats across your organisation’s environments before they cause damage and disruption. Complete the form to discuss your requirements with an MDR expert.
- 24/7 MDR solution
- Rated 9/10 for overall customer satisfaction
- CREST-accredited Security Operations Centre
- $1 Million incident protection warranty
Resources

























